Published on May 24, 2025
Burp Suite on Kali Linux: A Complete Guide to Web Application Security Testing
Burp Suite is one of the most popular penetration testing tools for web applications. Developed by PortSwigger, it offers a range of features that allow security testers to analyze, intercept, and modify web traffic between a browser and a target server. In this article, we will discuss how to use Burp Suite on Kali Linux, a Linux distribution specifically designed for penetration testing.
Installing Burp Suite on Kali Linux
Kali Linux, as a distribution designed for security, already includes Burp Suite Community Edition as part of its default package. To verify whether Burp Suite is installed, you can open a terminal and type the following command:
burpsuite
If Burp Suite is installed, the user interface will open. If not, you can install it with the command:
sudo apt update
sudo apt install burpsuite
Starting Burp Suite
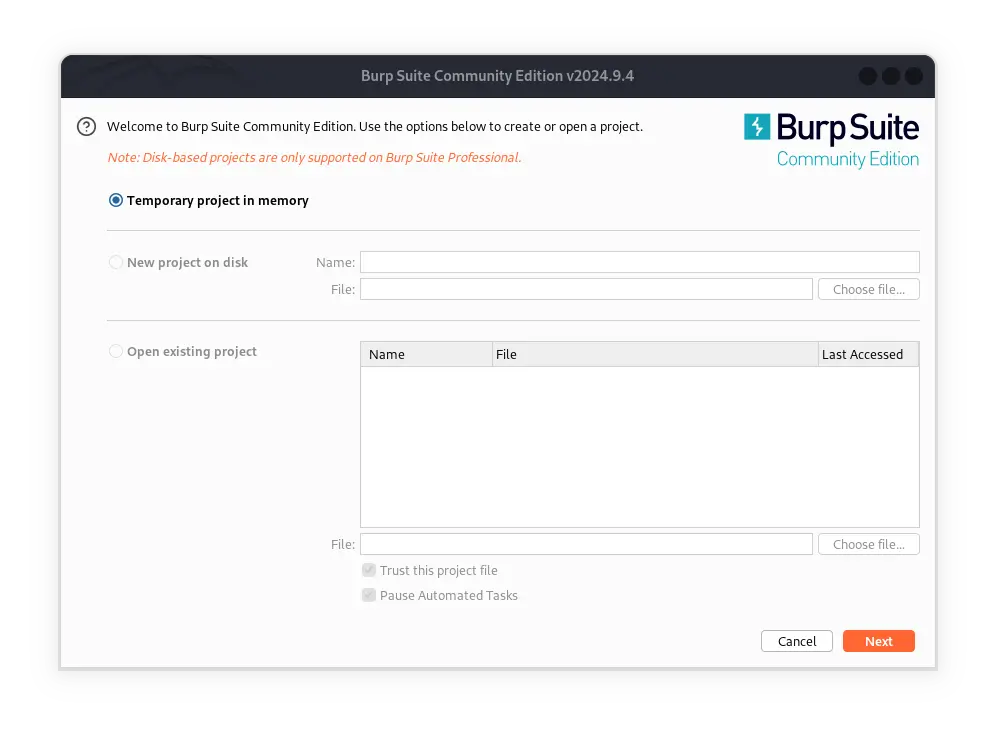
After installation, you can start Burp Suite through the terminal with the burpsuite command. When you first run Burp Suite, you will be presented with a wizard to choose a new or existing project. Select the “Temporary Project” option to start working without saving your project settings.
Configuring Your Browser to Use Burp Suite
To take advantage of Burp Suite features like intercepting web requests, you need to configure your browser to use Burp Suite as a proxy. Here are the steps:
- Open Proxy Settings in Browser
- In Firefox, go to
Preferences>Network Settings>Settings. - In Chrome, you can use an extension like “SwitchyOmega” to set the proxy.
- Set Proxy to Burp Suite
- HTTP proxy:
127.0.0.1with port8080. - Make sure to enable the “Use this proxy server for all protocols” option.
- Disable Proxy for Local: Add
localhost, 127.0.0.1to the exception list. - Save and Close Settings
Using Burp Suite for Testing
After configuring your browser, you can start using Burp Suite to intercept and analyze HTTP requests and responses.
- Interception
- Enable the
Proxytab in Burp Suite and clickIntercept is on. - Every HTTP request from the browser will be intercepted and displayed in this tab.
- HTTP History: All requests that have passed through the proxy can be viewed in the
HTTP historytab underProxy. - Repeater: Use the
Repeatertab to re-send the captured HTTP requests with certain modifications. This is useful for testing different inputs against the server. - Intruder: The
Intrudertab is used to automate testing by sending different variations of inputs to the web application. You can use it to find security vulnerabilities such as SQL injection or XSS. - Scanner: The Professional version of Burp Suite has a
Scannerfeature that can automatically find vulnerabilities in web applications. However, this is not available in the Community Edition.
Additional Features
- Decoder: This tab allows you to decode or encode data in various formats such as Base64, URL, or HTML.
- Comparer: Used to compare two sets of data, very useful for seeing the difference in HTTP responses before and after an action.
Tips and Tricks
- Use Extensions: Burp Suite has various extensions that can be added to extend its functionality, such as the Extender BApp Store .
- SSL Certificate: If you are facing issues with HTTPS websites, install the Burp Suite certificate into your browser to prevent SSL errors.
Conclusion
Burp Suite is a very powerful tool for web application security testing. By understanding how it works in Kali Linux, you can leverage its potential to find and mitigate vulnerabilities in your web applications. Although the Community Edition has limitations, many important features are still accessible and can be used effectively. Always ensure you have the appropriate permissions before performing penetration testing to comply with the law and professional ethics.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…