Published on May 28, 2025
CrackMapExec on Kali Linux: Complete Guide
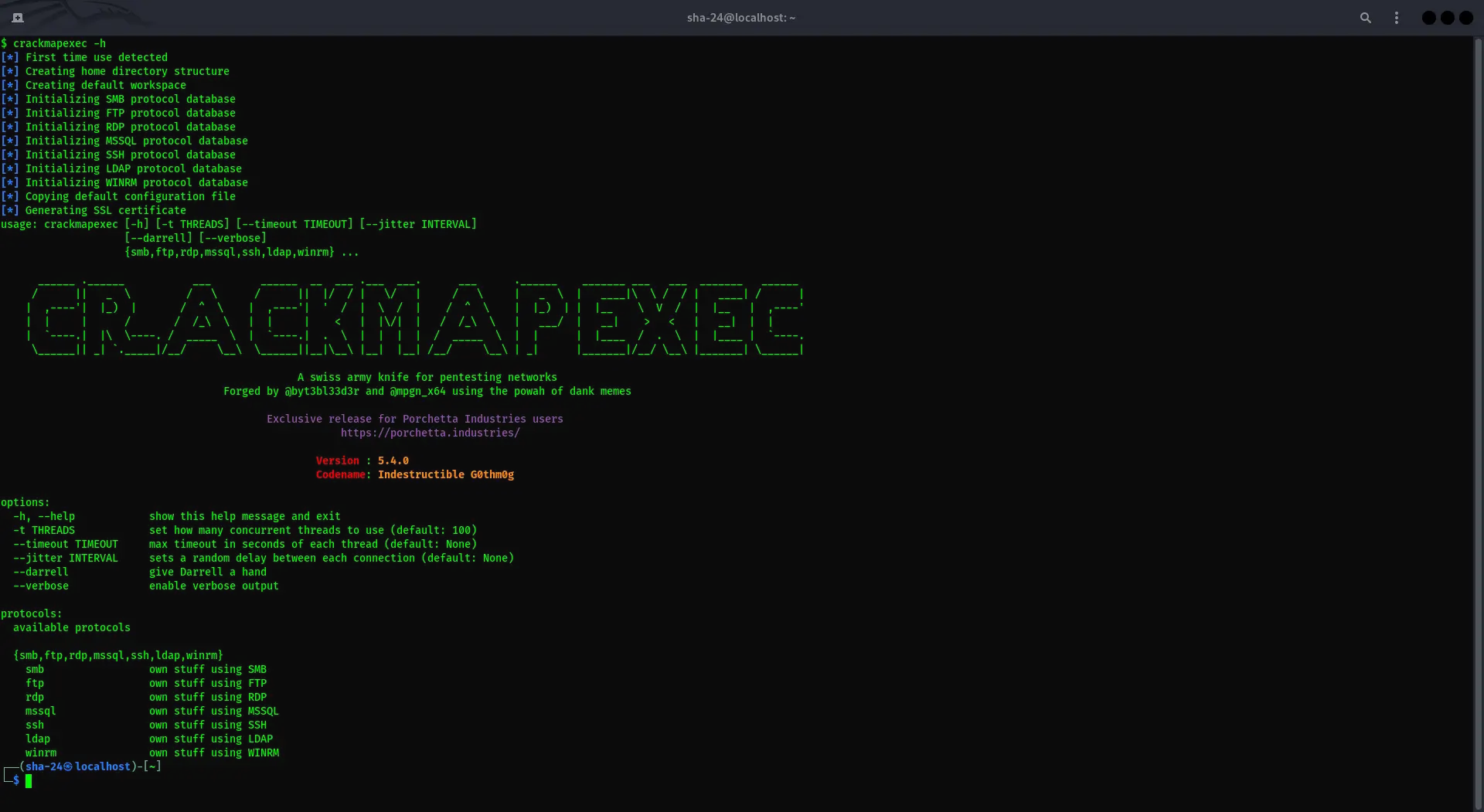
CrackMapExec (CME) is a multi-purpose tool used by security professionals to audit Active Directory environments and test network security. CrackMapExec is often used in penetration testing to automate tasks such as network enumeration, exploitation, and post-exploitation.
CrackMapExec Key Features
- Network Enumeration: CrackMapExec can scan and identify devices on a network, including servers, workstations, and other devices.
- Credential Management: The tool is capable of managing and testing credentials to gain access to targeted systems.
- Exploitation: CrackMapExec supports a variety of exploits, including remote command execution on vulnerable systems.
- Compatibility: CME supports a variety of protocols such as SMB, SSH, LDAP, and WinRM, making it very flexible in various network scenarios.
Installing CrackMapExec on Kali Linux
- Prerequisites
Before installing CrackMapExec, make sure your system has Python 3 and pip installed. Kali Linux usually has Python 3 installed by default.
- Installation Steps
- Update System
sudo apt update && sudo apt upgrade -y
- Install Dependencies
sudo apt install -y python3 python3-pip python3-dev build-essential libssl-dev libffi-dev
- Clone CME Repository
git clone https://github.com/byt3bl33d3r/CrackMapExec.git
- Enter CME Directory
cd CrackMapExec
- Install CME
pip3 install .
- Verify Installation
crackmapexec --version
If the installation is successful, you will see the version of CrackMapExec installed.
CrackMapExec Usage
- Network Enumeration
Network enumeration is the first step in security testing. CME can be used to scan a network and identify connected devices.
Sample Command
crackmapexec smb 192.168.1.0/24
This command will scan the entire 192.168.1.0/24 subnet and display the devices found.
- Credential Testing
CME allows for automated credential testing of multiple systems.
Sample Command
crackmapexec smb 192.168.1.100 -u username -p password
This command will attempt to login to the system with the IP 192.168.1.100 using the given username and password.
- Remote Command Execution
Once you gain access, you can run remote commands on the target system.
Example Command
crackmapexec smb 192.168.1.100 -u admin -p password123 --exec-command "ipconfig"
This command will execute ipconfig on the target system and return the results.
CrackMapExec Use Case Studies
Case Study 1: Enterprise Network Security Evaluation
In this scenario, a cybersecurity team uses CME to evaluate the security of their enterprise network. Using CME’s credential enumeration and testing features, they are able to quickly identify weak systems that are vulnerable to brute-force attacks.
Case Study 2: Insider Attack Simulation
The security team runs an insider attack simulation to assess the potential impact if an unauthorized employee gains access to admin credentials. Using CME, they can simulate the exploitation of internal systems to identify vulnerabilities that need to be fixed.
Best Practices for Using CrackMapExec
- Use in a Closed Environment: Always use CME on a network that you own or where you have explicit permission to use it.
- Comply with Ethics and Laws: Ensure that your use of CME complies with local laws and regulations as well as professional ethical standards.
- Update Regularly: CrackMapExec is a constantly updated tool. Make sure to always use the latest version to get the latest features and fixes.
Conclusion
CrackMapExec is a very powerful tool for network security testing, especially in Active Directory environments. With features like network enumeration, credential testing, and remote command execution, CME makes it easy for penetration testers to identify and exploit vulnerabilities in a network. However, it is important to use this tool ethically and legally.
With this guide, you now have a basic understanding of CrackMapExec in Kali Linux and how to use it in security testing. Always make sure to use this tool responsibly and only in authorized contexts.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…