Published on May 24, 2025
DirBuster on Kali Linux: The Complete Guide
DirBuster is one of the most popular tools in the cybersecurity community, especially for those working in penetration testing and web application security testing. This tool is developed by OWASP (Open Web Application Security Project) and is used to detect hidden directories and files on web servers. This article will discuss DirBuster in depth, including how to install, use, and interpret the results on Kali Linux .
What is DirBuster?
DirBuster is a Java application that performs brute force attacks to find hidden directories and files on web servers. This tool can help penetration testers find potential entry points into a system that are undetectable to the average user. DirBuster uses a customizable wordlist to match URLs that may exist on the server.
Key Features of DirBuster
- Brute Force and Wordlist Attack: DirBuster allows you to use brute force attacks or wordlist-based attacks to find hidden directories and files.
- Multi-threading: The tool supports multi-threading, which speeds up the search process by running multiple queries simultaneously.
- Custom Wordlists: You can use the provided wordlists or create your own.
- Save and Resume Ability: DirBuster allows you to save your session and resume later without losing the results you have obtained.
Installing DirBuster on Kali Linux
DirBuster is usually installed by default on Kali Linux. However, if the tool is not available, you can install it with the following steps:
- Ensure Java is Installed
DirBuster requires Java to run. You can check if Java is installed with the command:
java -version
If Java is not installed, you can install it with the command:
sudo apt update
sudo apt install default-jre
- Downloading DirBuster
You can download DirBuster from the OWASP website or using the Kali Linux repositories. Use the following command to download and install it:
sudo apt install dirbuster
Using DirBuster
Once the installation is complete, you can run DirBuster with the command:
dirbuster
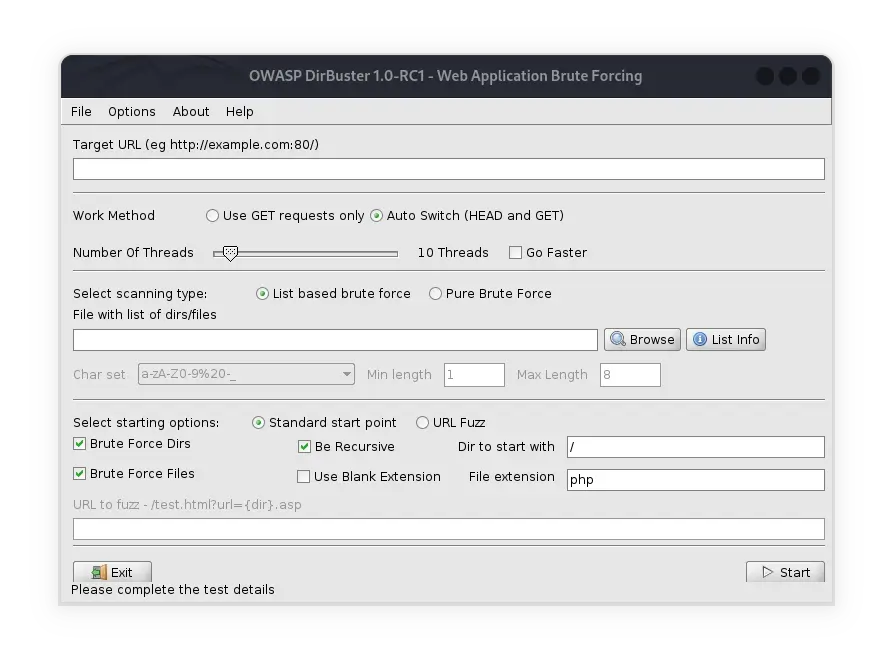
This will open the DirBuster graphical interface. Here are the basic steps to use DirBuster:
- Enter Target URL
At the top of the DirBuster window, enter the target URL you want to attack.
- Select Attack Type
You can choose between a brute force attack or using a word list. For the word list, you can use the list that is already in the tool or load your own custom list.
- Configure Options
You can adjust various options such as the number of threads, request method (GET or POST), and so on.
- Start Attack
Click the “Start” button to begin the scanning process. DirBuster will start sending requests to the target server to find hidden directories and files.
Understanding DirBuster Results
After the attack is complete or during the attack, DirBuster will display the results in the form of a list of directories and files found. The information provided includes:
- URL: The location of the directory or file found.
- Status: The HTTP status code returned by the server (e.g., 200 for “OK”, 404 for “Not Found”).
- Response Time: The time it took for the server to respond to the request.
- Size: The size of the response received from the server.
Best Practices for Using DirBuster
- Use the Right Word List: Make sure to use a word list that is relevant to the application you are attacking. Common word lists may not always be effective.
- Proper Configuration: Adjust the number of threads according to the capacity of your system and the target server to avoid overloading both sides.
- Save Session: Save your session periodically to avoid data loss in case of a compromise.
- Respect Ethics: Always get permission before performing penetration testing on a system that is not yours.
Conclusion
DirBuster is a very useful tool in penetration testing and securing web applications. Using DirBuster, testers can quickly find hidden directories and files that can be security holes. Proper and ethical use of DirBuster can help in improving the security of web servers and online applications.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…