Published on May 24, 2025
Understanding DNS Rebinding Attacks and Their Implementation in Kali Linux
DNS Rebinding is an attack technique that exploits the Domain Name System (DNS) to run malicious code in the victim’s web browser, which is then used to attack devices on the victim’s private network. This attack allows the attacker to access internal resources that would otherwise be inaccessible from outside the network. This article will take a deep dive into the DNS Rebinding attack, how it works, its impact, and how to implement and analyze this attack using the tools available in Kali Linux.
What is DNS Rebinding?
DNS Rebinding is a method of manipulating domain name resolution that is used as a form of computer attack. In this attack, a malicious web page causes visitors to run a client-side script that attacks other machines on the same network. While the same-origin policy (SOP) prevents this by restricting script access to only the same host, DNS Rebinding circumvents this protection by abusing DNS.
How DNS Rebinding Works
Here are the general steps in a DNS Rebinding attack:
- Domain Registration: The attacker registers a domain (for example, attacker.com) and points the domain to a DNS server controlled by the attacker.
- Initial DNS Response: When the victim accesses attacker.com, the attacker’s DNS server responds with the IP address of the server hosting the malicious code, with a very low Time To Live (TTL) to prevent caching.
- Malicious Code Execution: The victim’s browser loads malicious code (e.g., JavaScript ) from attacker.com.
- DNS Re-Request: The malicious code makes an additional request to attacker.com. Since the TTL is low, the browser makes a new DNS request.
- DNS Response Change: The attacker’s DNS server responds with a new IP address, such as the victim’s internal network IP address.
- Internal Resource Access: The malicious script can now access internal resources through the victim’s browser, bypassing the SOP policy.
Impact of DNS Rebinding Attacks
DNS Rebinding attacks can have a variety of serious impacts, including:
- Bypass Firewall: The attacker can access internal devices that are usually protected by a firewall.
- Data Theft: Accessing and stealing sensitive data from the victim’s internal network.
- IoT Device Control: Taking over Internet of Things (IoT) devices on the victim’s network, such as security cameras or smart thermostats.
- Advanced Attacks: Using the victim’s browser as a proxy to launch further attacks, such as Distributed Denial of Service (DDoS).
Tools for DNS Rebinding in Kali Linux
Kali Linux , as a security-focused Linux distribution, provides a variety of tools that can be used to analyze and implement DNS Rebinding attacks. Here are some relevant tools:
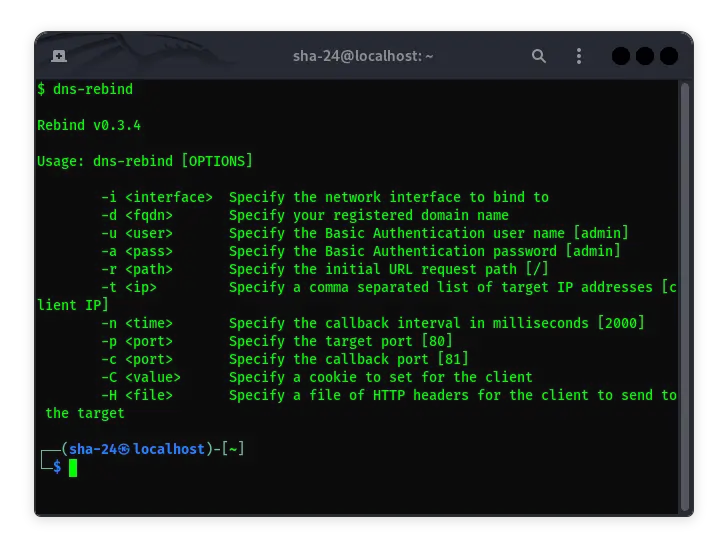
1. Rebind
Rebind is a tool that implements a DNS Rebinding attack using multiple A records. Although the tool was originally written to target home routers, it can be used to target other public IP addresses.
Example Usage:
Using the eth0 interface to perform a rebind attack with the kali.local domain:
rebind -i eth0 -d kali.local
This command will start a DNS server on port 53, an attack web server on port 80, a callback web server on port 81, and a proxy server on the specified IP address.
2. Singularity
Singularity is a DNS Rebinding attack framework developed by the NCC Group . The tool includes the necessary components to change the IP address of the attack server’s DNS name.
Key Features:
Supports a variety of rebinding techniques.
Easy to configure and use.
Provides a web interface to monitor and control attacks.
3. DNSRecon
DNSRecon is a tool used to perform DNS enumeration. Although not a specific tool for DNS Rebinding attacks, DNSRecon can be used to gather necessary information before launching an attack, such as zone records, SRV records, and more.
Example Usage:
Performing a standard enumeration on a target domain:
dnsrecon -d target.com
This command will gather information such as SOA, NS, A, AAAA, MX, and SRV records from the target domain.
Preventing DNS Rebinding Attacks
To protect your network and devices from DNS Rebinding attacks, the following steps can be taken:
- Secure DNS Configuration: Use a DNS server that filters private IP addresses and loopbacks in DNS responses.
- Proper Firewall Settings: Configure your firewall to block requests from untrusted sources and monitor suspicious traffic.
- Software Updates: Ensure all devices and applications are updated with the latest security patches to reduce vulnerabilities.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…