Published on May 24, 2025
Enum4linux in Kali Linux: Complete Guide
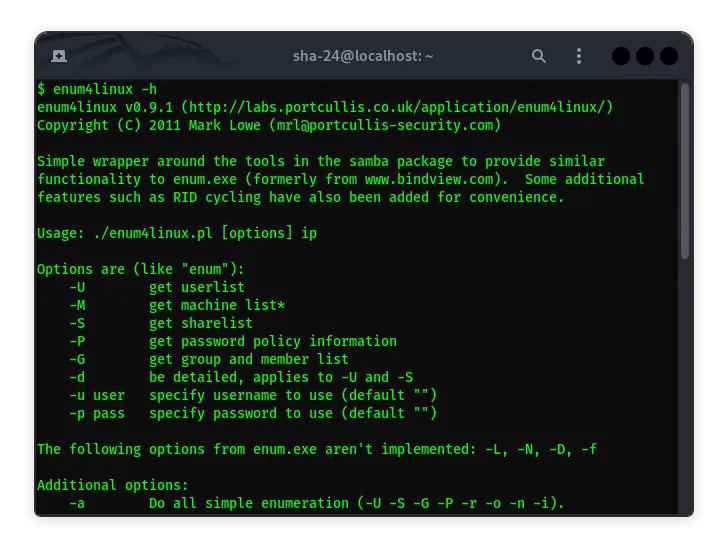
Enum4linux is a script-based tool used to enumerate information from Windows servers and Samba-based systems. This tool is very useful for information security professionals, especially when conducting penetration testing on networks that include Windows servers. This article will discuss in detail about using Enum4linux in Kali Linux, how to install it, and how to use it for various enumeration purposes.
What is Enum4linux?
Enum4linux is a Python-based script that utilizes tools such as smbclient, rpcclient, and net to obtain various information from Windows servers or Samba-based systems. Using Enum4linux, we can enumerate:
- List of users
- User groups
- Directory shares
- Password policies
- Domain and workstation information
This tool is very useful for footprinting the target network, providing important information that can be used for the next attack step.
Installing Enum4linux in Kali Linux
Kali Linux , as a Linux distribution specifically designed for penetration testing, is equipped with various security tools. However, if Enum4linux is not installed, we can easily install it using the following steps:
- Updating Repository: Before installing, make sure your Kali Linux system is updated to the latest version.
sudo apt update && sudo apt upgrade -y
- Downloading Enum4linux: Enum4linux can be downloaded directly from GitHub or its official website.
git clone https://github.com/CiscoCXSecurity/enum4linux.git
- Go to Directory and Run: Once the download is complete, go to the Enum4linux directory and run the script.
cd enum4linux
./enum4linux.pl
Enum4linux uses bahasa Perl , so you must make sure that Perl is installed on your system. Usually, Perl is included in the standard Kali Linux installation.
- Easy Guide to Handling Bugs in Software Development
- I Asked, Is ChatGPT the Strongest AI Right Now? This is Answered
- What Is Hugo? A Complete Guide to Understanding the Popular Static Site Generator
- Free VPN: Protecting You or Putting Your Data at Risk?
- What Is the Difference Between Phishing and Malware?
Using Enum4linux
Enum4linux has many options that allow users to perform various types of enumeration. Here are some examples of using Enum4linux along with detailed explanations.
- Basic Enumeration: To perform basic enumeration of a server, we can run the following command:
./enum4linux.pl <Target IP Address>
This command will provide basic information such as a list of users, directory shares, and domain information.
- Getting a List of Users: To get a list of users from a Windows server, we can use the
-Uoption.
./enum4linux.pl -U <Target IP Address>
This option tries to get user information via SMB and RPC protocols.
- Group Enumeration: Using the
-Goption, Enum4linux can retrieve information about user groups present on the server.
./enum4linux.pl -G <Target IP Address>
- Password Policy Check: To check the password policy on the target server, we can use the
-Poption.
./enum4linux.pl -P <Target IP Address>
This option helps identify policies that may be weak and could be an entry point for attackers.
- SMB Share Enumeration: The
-Soption is used to get information about SMB shares present on the target server.
./enum4linux.pl -S <Target IP Address>
This is very useful for finding directories or files that can be accessed without authentication.
- Full Information: To get all the information that can be collected, we can use the
-aoption.
./enum4linux.pl -a <IP Address Target>
This option runs all available enumeration methods, giving very detailed output.
Enum4linux Output Analysis
After running Enum4linux, we will get a fairly long and detailed output. Here is how to analyze some important parts of the output:
- User List: This information can be used to try brute force or social engineering attacks. Usually, Enum4linux will display the username along with their description.
- Directory Share: The shares found can be explored further to find sensitive files or incorrect configurations.
- Password Policy: Weak password policies can be a loophole for password guessing or brute force attacks.
- Domain Information: Domain information such as domain name, SID, and others can be used for further attacks, such as attempting to take control of the domain controller.
Security and Ethics
It is important to remember that the use of Enum4linux, like any other penetration testing tool, must be done with the permission of the network owner. Performing enumeration without permission can be considered illegal activity and can potentially result in legal consequences.
Conclusion
Enum4linux is a very useful tool for enumerating Windows servers and Samba-based systems. With its comprehensive features and ability to extract important information, this tool is a mainstay for penetration testers. However, ethical and legal use should still be a top priority. With a thorough understanding and proper use, Enum4linux can provide valuable insights that support effective security testing.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…