New Post

What is an XSS Attack? And How to Deal with It?
Syukra
In the world of web security, Cross-Site Scripting (XSS) is one of the most common and potentially damaging types of attacks. XSS is a type of attack in which …
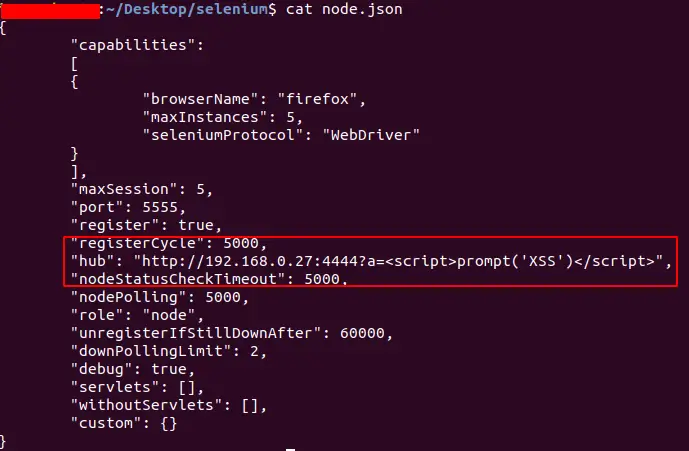
XSS Payload: Understanding, Risks, and Examples
Syukra
Cross-Site Scripting (XSS) is one of the most common types of cyber attacks on web applications. XSS allows attackers to inject malicious scripts into a web …

Easy Guide to Handling Bugs in Software Development
Syukra
In software development, bugs are a common problem that is often encountered. Bugs can range from minor issues that do not have a significant impact to major …

Why is Monero Famous for its High Level of Security Compared to Other Cryptocurrencies?
Syukra
Monero (XMR) is one cryptocurrency that is often referred to as the gold standard when it comes to privacy and security. Introduced in 2014, Monero was designed …

WPScan: Identify and Secure WordPress from Vulnerabilities
Syukra
WordPress has become one of the most popular platforms for building websites worldwide. From personal blogs to large e-commerce sites, WordPress offers …

Meet CrowdStrike: The Modern Cybersecurity Leader
Syukra
In the ever-evolving digital era, cyber threats are increasingly complex and widespread. Companies, government institutions, and other organizations face …
