Published on Apr 11, 2025
Types of Security Encryption: Definition, How It Works, and Examples
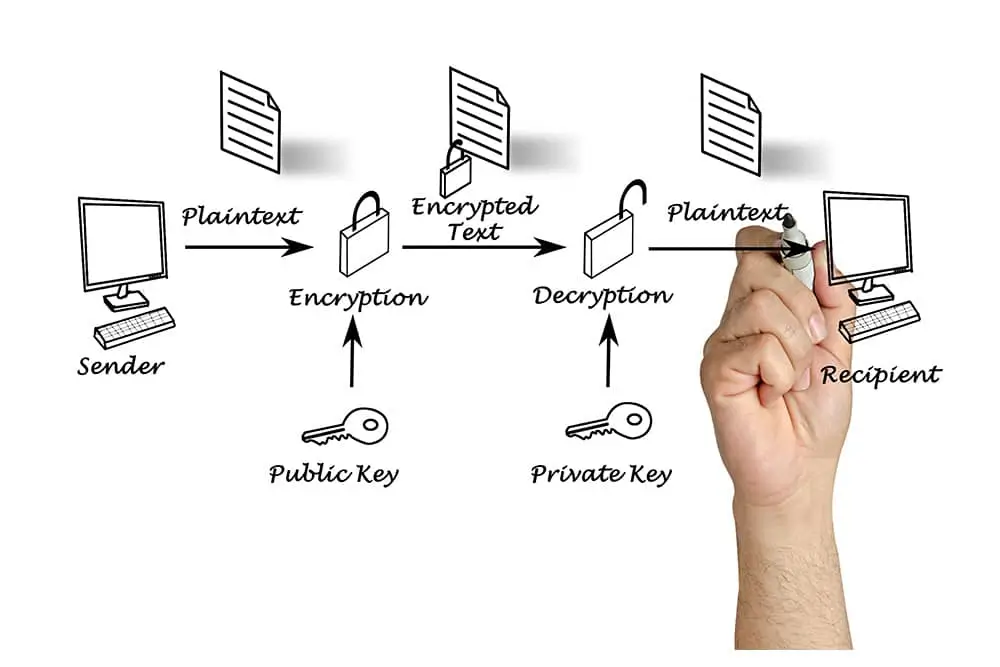
Encryption is a data security technique that aims to protect information so that it can only be accessed by authorized parties. In today’s digital world, encryption is the main key to ensuring data security, especially in financial transactions, personal communications, and storing important data. Encryption works by changing the original data (plaintext) into an unreadable form (ciphertext), and can only be changed back to its original form using a specific key.
Here are the most common types of encryption and how they work:
1. Symmetric Encryption
Symmetric encryption uses the same key for both encryption and decryption. This type of encryption is generally faster and more efficient than other methods, but has risks if the key is leaked or falls into unauthorized hands.
How it Works
In symmetric encryption, the same key is used by the sender to encrypt data and by the recipient to decrypt it. Because it only uses one key, the encryption and decryption processes are faster. However, the weakness is that if the key is known to a third party, the data can be read by unauthorized people.
Algorithm Examples
- AES (Advanced Encryption Standard): This algorithm is one of the most popular encryption standards in the world today, used by governments, militaries, and large companies. AES has various key sizes, such as 128-bit, 192-bit, and 256-bit, with varying levels of security.
- DES (Data Encryption Standard): Before AES, DES was a commonly used encryption standard. DES uses a 56-bit key, but is currently considered less secure due to advances in computing technology that can easily break this key.
- Blowfish: A symmetric encryption algorithm that is faster than DES and is often used for software applications because of its flexibility and speed.
2. Asymmetric Encryption
Unlike symmetric encryption, asymmetric encryption uses two different but paired keys: a public key and a private key. The public key can be freely shared, while the private key must be kept secret.
How It Works
In asymmetric encryption, data encrypted using a public key can only be decrypted using the corresponding private key, and vice versa. This makes asymmetric encryption more secure for transmitting sensitive data over the internet, such as in banking and e-commerce transactions.
Algorithm Examples
- RSA (Rivest-Shamir-Adleman): RSA is one of the most well-known asymmetric encryption algorithms. It uses long keys (1024-bit, 2048-bit, or even more) which makes it very secure for internet communications.
- DSA (Digital Signature Algorithm): DSA is used primarily to create digital signatures, which ensure the authenticity and integrity of messages sent. DSA is often used in conjunction with RSA to add an additional layer of security.
3. Hashing Encryption
Hashing is not strictly an encryption method, but rather a technique for mapping data into a fixed code or hash. Hashed data cannot be returned to its original form, making it suitable for storing sensitive data that does not need to be decrypted, such as passwords.
How it Works
Hashing works by converting input data into a fixed-length string called a hash. For example, a user’s password will be hashed and the resulting hash is stored in the system, not the original password. When the user logs in, the password entered will be hashed and compared to the stored hash.
Algorithm Examples
- MD5 (Message Digest Algorithm 5): MD5 produces a 128-bit hash. However, this algorithm has been found to have security weaknesses so it is rarely used for high security applications.
- SHA-1 and SHA-256 (Secure Hash Algorithm): SHA-1 is more secure than MD5, but weaknesses have also been found in this algorithm in recent times. SHA-256, part of the SHA-2 family, is more popular and widely used in modern applications due to its better security.
4. Hybrid Encryption
Hybrid encryption is a combination of symmetric and asymmetric encryption to take advantage of the strengths of each. This method is used in many modern internet security protocols, such as SSL/TLS.
How it Works
In hybrid encryption, a public key is used to encrypt a symmetric key that will be used for data communication. After the symmetric key is encrypted and sent to the recipient, the subsequent encryption and decryption of the data is done with symmetric encryption. This allows for higher security and better speed.
Example of Use
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): SSL/TLS is a security protocol used to secure internet connections. This protocol uses hybrid encryption to protect sensitive data when communicating between a client and a server, such as when accessing a banking or e-commerce website.
5. Quantum Encryption
Quantum encryption is a type of encryption that uses the principles of quantum mechanics to create secure keys. This technology is still in its infancy and has not been widely implemented, but it is expected to become the security standard of the future.
How it Works
Quantum encryption uses quantum physics phenomena such as superposition and entanglement to generate and transmit encryption keys. One of the underlying technologies is Quantum Key Distribution (QKD), which allows two parties to securely share keys.
Example
- BB84: The first quantum encryption protocol developed in 1984 by Charles Bennett and Gilles Brassard. BB84 uses photons transmitted through a quantum channel to create highly secure encryption keys.
6. Homomorphic Encryption
Homomorphic encryption is a type of encryption that allows mathematical operations on encrypted data without having to decrypt it first. This type of encryption has great potential in cloud computing and data analytics because the data can be processed securely without the risk of leakage.
How it Works
In homomorphic encryption, the data is first encrypted, and then certain operations can be performed on the encrypted data. The results of these operations will remain encrypted, and when decrypted, the results will be the same as if the operations were performed on the original data.
Use Cases
Healthcare and Financial: Financial and healthcare institutions can leverage homomorphic encryption to process sensitive data such as medical records or financial statements without revealing personal information to third parties.
Conclusion
Each type of encryption has its own advantages and disadvantages, as well as its own uses. Symmetric encryption excels in speed, while asymmetric encryption offers higher security for data transfers. Hashing encryption is suitable for storing static data such as passwords, while hybrid encryption and quantum encryption offer more advanced security. Homomorphic encryption, while still in its infancy, promises to be a new way to secure data in the cloud computing era.
Proper use of encryption is a crucial part of data security. As technology advances and cybersecurity threats increase, more sophisticated types of encryption will continue to emerge to protect data from unauthorized access.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…