This is a list of posts with tags Cyber Security
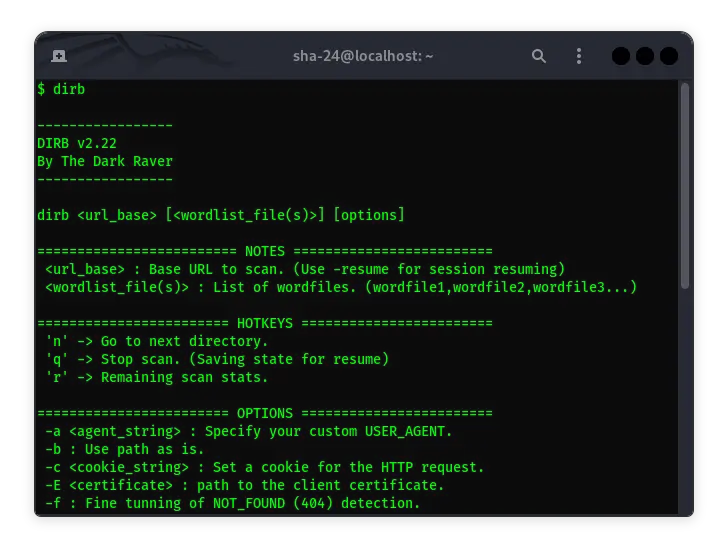
Dirb in Kali Linux: The Complete Guide
Dirb is one of the essential tools in the world of cybersecurity, especially for web penetration testing. This tool is known for its ability to find hidden …
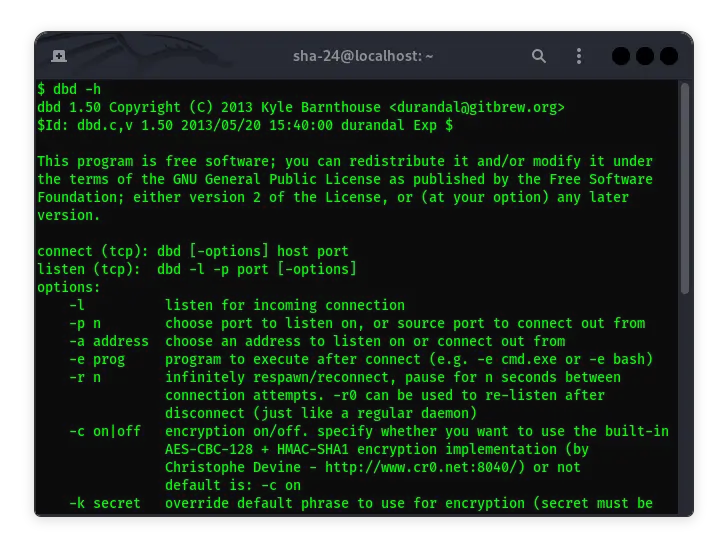
How to Use dbd Kali Linux
Kali Linux, the preferred distribution for penetration testers and cybersecurity professionals, comes equipped with a myriad of tools designed to facilitate …
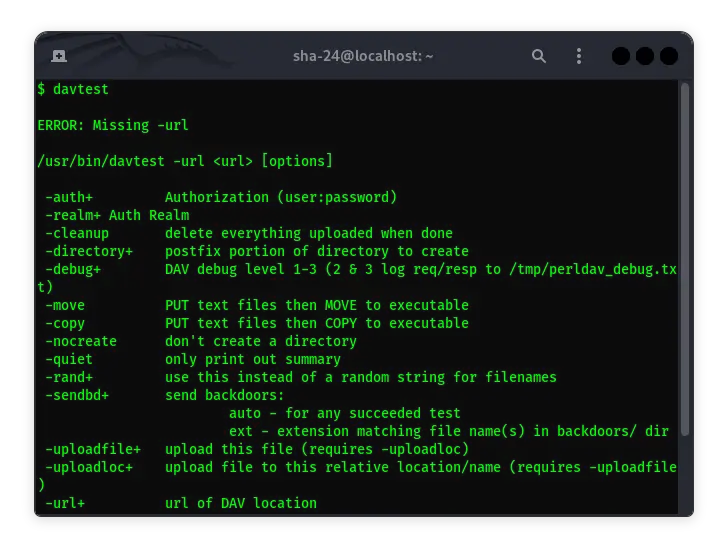
Complete Guide to Using Davtest on Kali Linux
Davtest is a network security tool used to test WebDAV servers. WebDAV (Web Distributed Authoring and Versioning) is an extension of the HTTP protocol that …
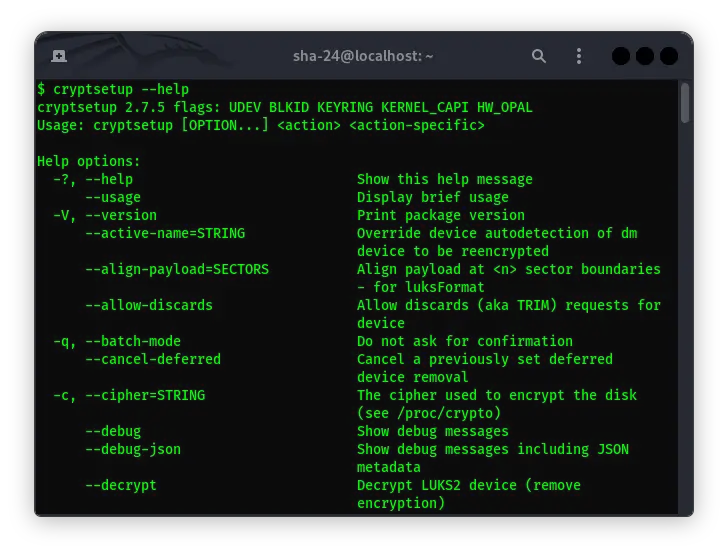
Complete Guide to Using Cryptsetup on Kali Linux
Data security is becoming increasingly important in this digital era. One way to protect data is through encryption. Kali Linux, as one of the most widely used …
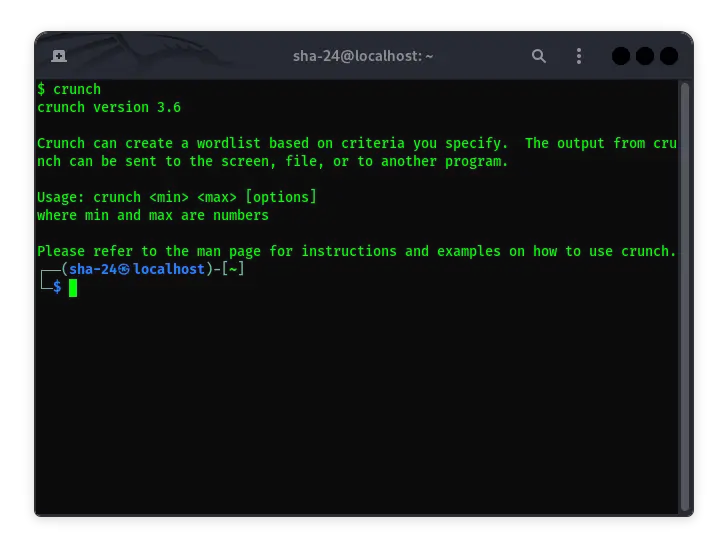
Crunch on Kali Linux: A Complete Guide to Using Password Generators
Kali Linux is known as one of the best Linux distributions for penetration testing and ethical hacking purposes. One of the tools that is often used in this …
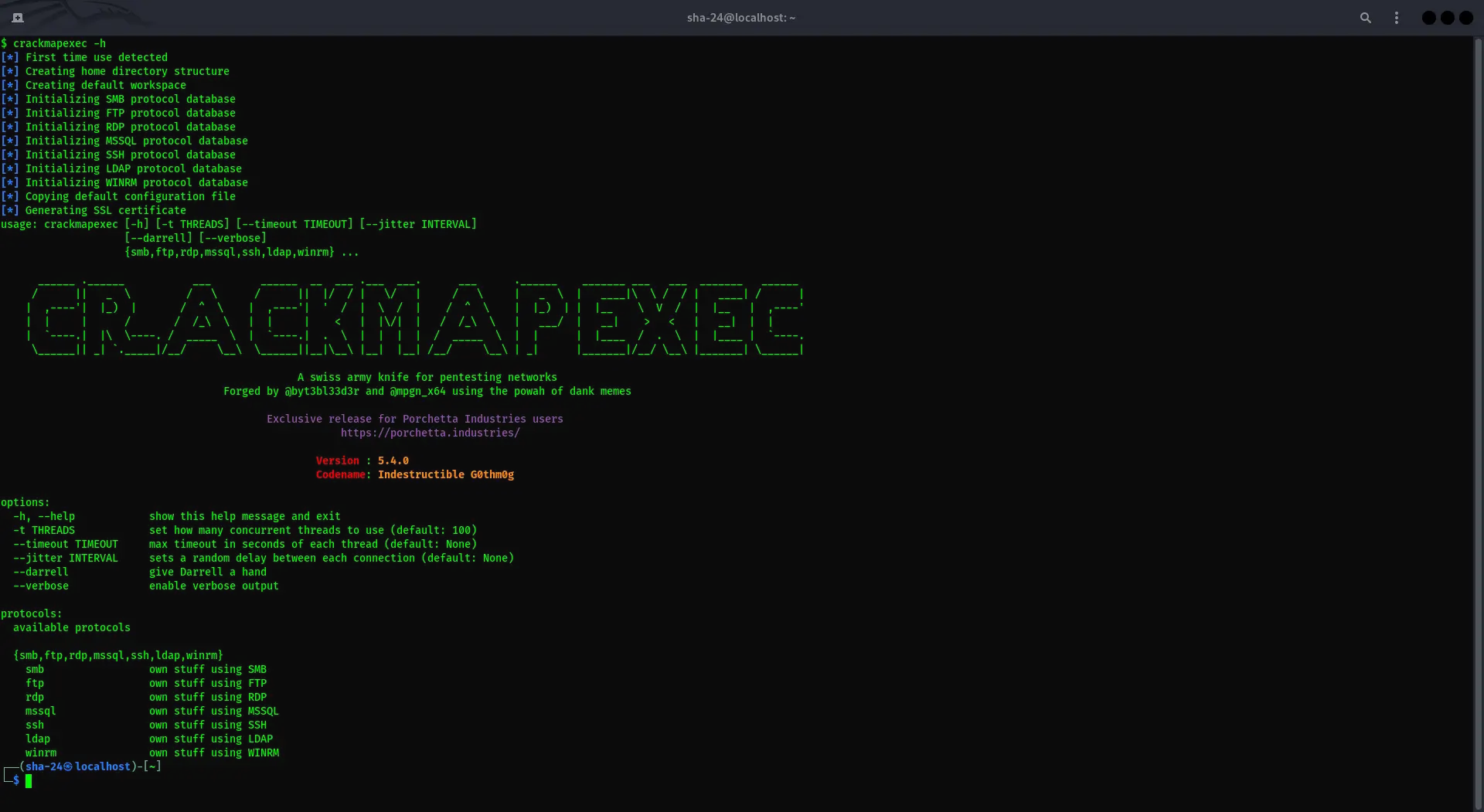
CrackMapExec on Kali Linux: Complete Guide
CrackMapExec (CME) is a multi-purpose tool used by security professionals to audit Active Directory environments and test network security. CrackMapExec is …