Published on May 24, 2025
What Is Ddos Attack?
DDoS (Distributed Denial of Service) attack is a type of cyber attack that aims to disrupt the services of a system, server, or network so that it cannot be accessed by legitimate users. This attack is carried out by flooding the target with very large internet traffic, exceeding the capacity that the target system can handle.
How DDoS Attacks Work
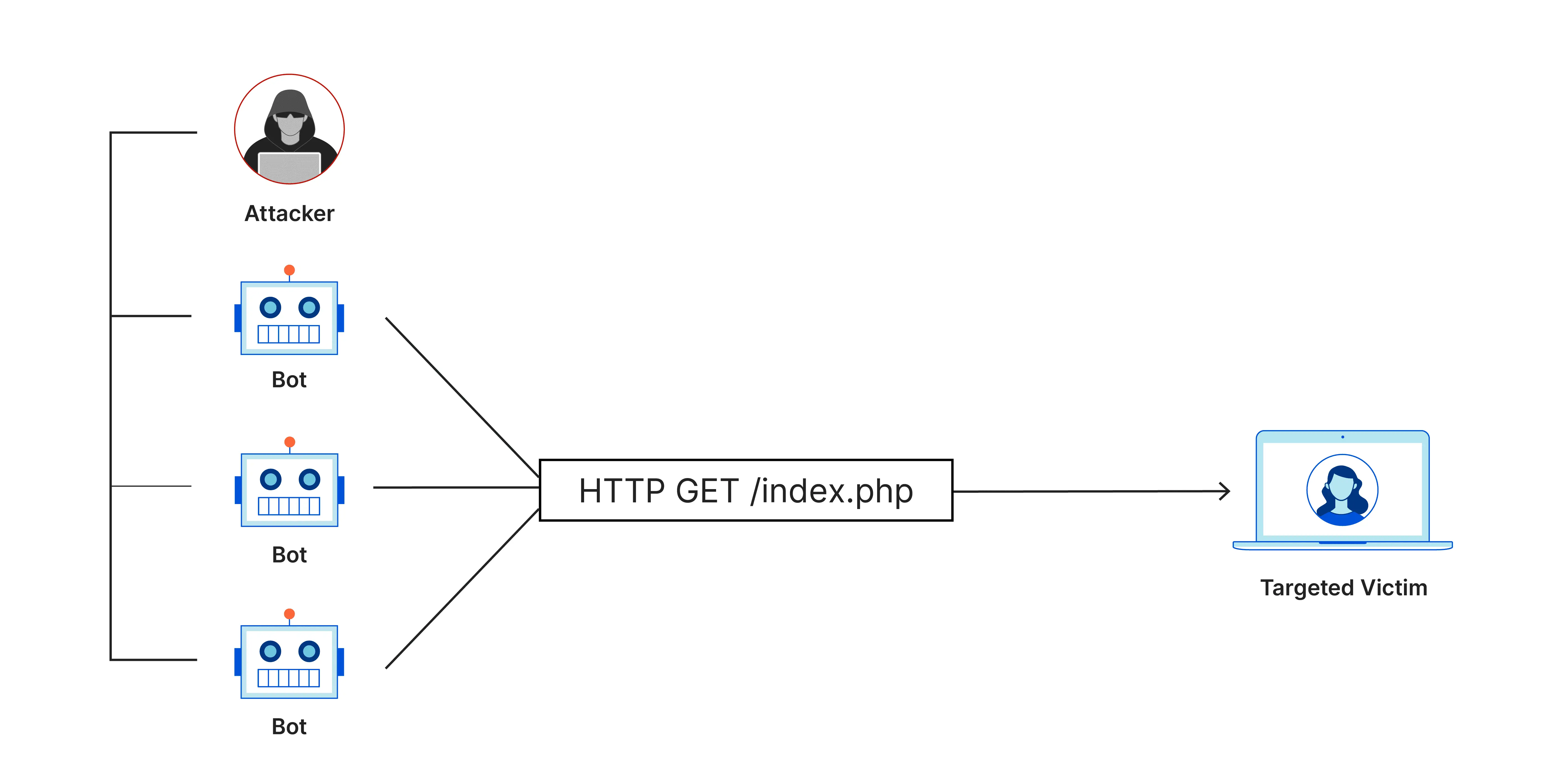
- Attack Distribution: DDoS attacks usually involve many computers that have been infected with malware and turned into botnets. Botnets are networks of computers controlled by attackers without the owner’s knowledge.
- Excessive Traffic Sending: The attacker instructs the botnet to send excessive requests to the target server simultaneously. This causes the server to be overwhelmed and unable to process legitimate requests from other users.
- Performance Decreased or Service Failure: Because the server or network cannot handle the very large volume of requests, its performance decreases drastically or even stops functioning altogether. This results in legitimate users being unable to access the service.
Types of DDoS Attacks
- Volume-based Attacks: These attacks aim to flood the network bandwidth by sending large amounts of data to the target. Examples of these attacks are ICMP floods and UDP floods.
- Protocol Attacks: These attacks exploit weaknesses in communication protocols to exhaust server resources. Examples are SYN flood and Ping of Death.
- Application Layer Attacks: These attacks target the web layer (application layer) applications and are more difficult to detect. Examples of these attacks are HTTP floods and Slowloris.
Impact of DDoS Attacks
- Financial Loss: Businesses that rely on online services can suffer significant financial losses due to service disruptions.
- Reputation: DDoS attacks can damage a company’s reputation, especially if the attacks last for a long time or occur frequently.
- Data Loss: In some cases, DDoS attacks can be used as a distraction to steal sensitive data from the target.
How to Deal with DDoS Attacks
- Using DDoS Protection Services: Many security service providers offer protection against DDoS by filtering malicious traffic before it reaches the target server.
- Hardening Infrastructure: Adding network and server capacity can help withstand a large DDoS attack.
- Monitoring and Early Detection: Using monitoring tools to detect early signs of a DDoS attack can help in responding quickly and minimizing its impact.
- Using a Firewall and Load Balancer: A firewall and load balancer can help filter out malicious traffic and distribute the traffic load evenly.
How to Protect Yourself from DDoS?
Protecting yourself from a Distributed Denial of Service (DDoS) attack requires a comprehensive, layered approach. Here are some steps you can take to protect your systems and networks from DDoS attacks:
1. Using DDoS Protection Services
DDoS protection services from a cybersecurity provider can help protect websites and applications from attacks. These services typically include real-time traffic monitoring and automated mitigation of attacks.
2. Configuring a Firewall and Intrusion Detection System (IDS/IPS)
- Firewall: Configure a firewall to filter out malicious traffic and limit the types of requests that can reach the server.
- IDS/IPS: Intrusion Detection and Prevention Systems can detect suspicious activity and block malicious traffic before it reaches its target.
3. Using a Load Balancer
Load balancer can distribute network traffic evenly across multiple servers. This helps prevent a single server from being overwhelmed with excessive traffic and increases resilience to DDoS attacks.
4. Using an Anycast Network
Anycast routing allows requests to be distributed across multiple geographic locations. This helps distribute the burden of a DDoS attack across multiple servers, reducing its impact on a single server or location.
5. Strengthening Infrastructure
- Scalability: Increase network and server capacity to handle sudden increases in traffic.
- Redundancy: Provide backup servers that can be activated in the event of an attack.
6. Configuring Rate Limiting
Rate limiting limits the number of requests a single user can send in a given time period. This can prevent a single user from sending too many requests at once.
7. Traffic Monitoring and Analysis
Continuous network traffic monitoring can help detect early signs of a DDoS attack. Traffic monitoring and analysis tools can help identify attack patterns and respond quickly.
8. Implement Strict Security Policies
Implement strict security policies and ensure all devices and systems are always updated with the latest security patches. This includes:
- Closing unnecessary ports.
- Using strong passwords and two-factor authentication (2FA).
- Limiting access to critical resources to authorized users only.
9. Increase Awareness and Training
Provide training to staff on the DDoS threat and how to identify the signs of an attack. Awareness of the threat and a quick response can reduce the impact of an attack.
10. Use Cloud-based Protection
Many cloud providers offer integrated DDoS protection solutions. These solutions can absorb and mitigate DDoS attacks before they reach your core infrastructure.
11. Have an Attack Response Plan
Have a clear and structured response plan in place in the event of a DDoS attack. This plan should include steps to identify the attack, mitigate its impact, and restore service as quickly as possible.
What are some famous DDoS attacks?
Some famous DDoS attacks that have occurred in recent years show how serious this threat is and the impact it can have. Here are some of them:
1. DDoS attack on Dyn (2016)
On October 21, 2016, DNS service provider Dyn fell victim to one of the largest DDoS attacks ever. The attack was carried out using the Mirai botnet, which consisted of IoT devices infected with malware. The attack caused major disruptions to popular websites including Twitter, Reddit, Netflix, and Spotify. As a result, many users in the United States and Europe experienced difficulty accessing these services for several hours.
2. DDoS attack on GitHub (2018)
In February 2018, GitHub, a source code hosting platform, suffered a massive DDoS attack with peak traffic reaching 1.35 Tbps (terabits per second). This attack was one of the largest in history and used the “memcached reflection” technique to increase traffic volume. Although the attack only lasted about 20 minutes, its impact was significant enough to require assistance from Akamai Prolexic to mitigate the attack.
3. DDoS attack on Estonia (2007)
In April 2007, Estonia experienced a series of DDoS attacks targeting government websites, banks, and media outlets. The attacks lasted for several weeks and were one of the earliest examples of a nationwide cyberattack. The attacks were thought to be related to the political dispute between Estonia and Russia, and caused significant disruption to the country’s internet infrastructure.
4. DDoS attack on Cloudflare (2020)
In August 2020, Cloudflare, a company that provides DDoS protection services, reported that they had successfully mitigated one of the largest DDoS attacks ever recorded. The attack peaked at 1.02 Tbps and lasted for several hours. Cloudflare was able to withstand this attack thanks to their advanced DDoS mitigation technology and infrastructure.
5. BBC DDoS attack (2015)
On 31 December 2015, the BBC website was the target of a massive DDoS attack that rendered the site inaccessible for several hours. The attack was allegedly carried out by a hacker group calling themselves “New World Hacking”, who claimed the attack was a test of their skills.
6. Spamhaus DDoS attack (2013)
Spamhaus, an organization dedicated to combating internet spam, suffered a major DDoS attack in March 2013. The attack peaked at 300 Gbps (gigabits per second) and was one of the largest DDoS attacks of its time. The attack involved a technique called DNS Amplification, which allows attackers to increase the volume of traffic directed at a target.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…