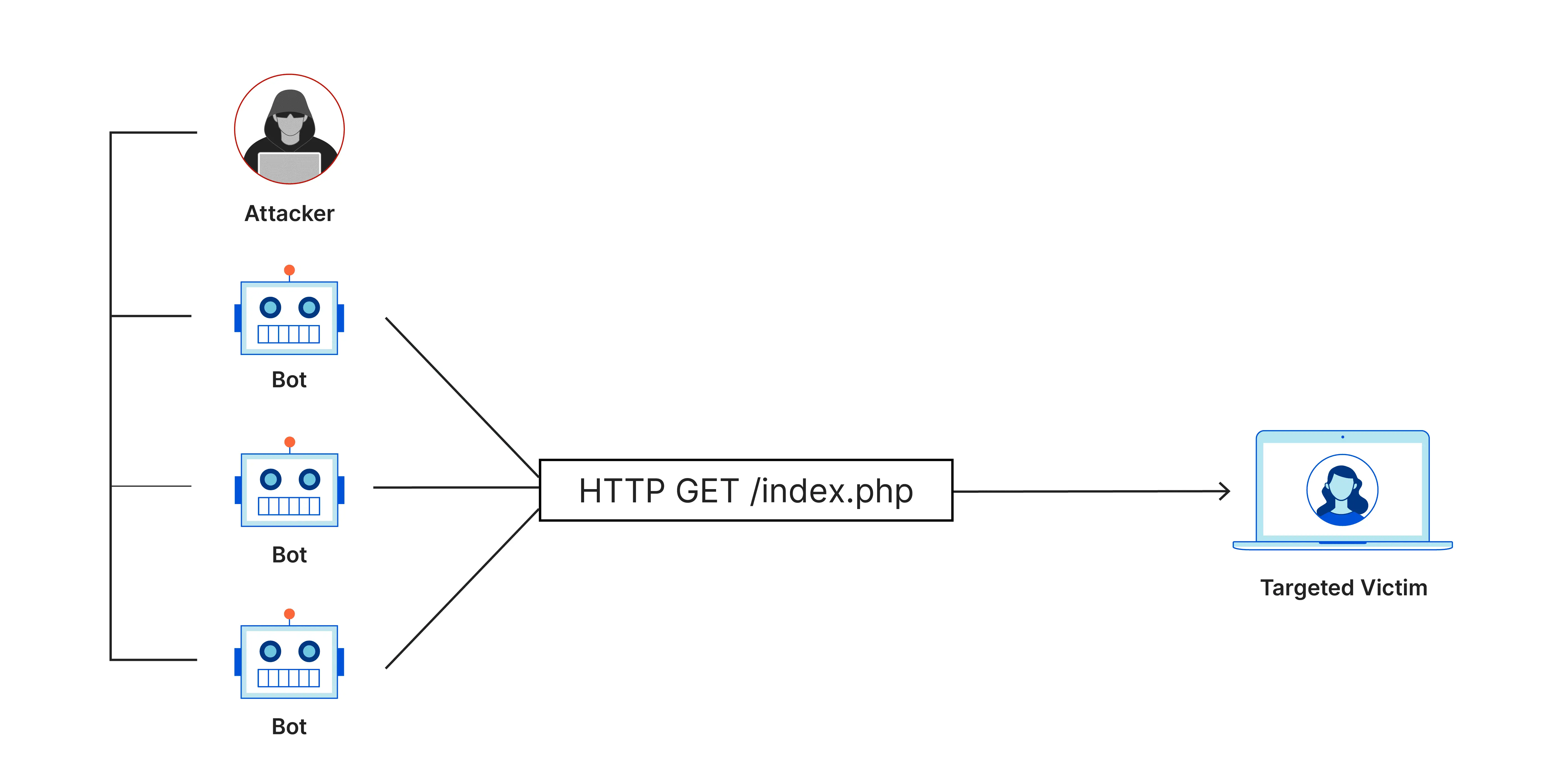
Published on May 24, 2025
What Is Delta Exploit?

Delta exploit is a term used in cybersecurity to refer to a type of exploit that takes advantage of a gap or vulnerability in software or a system. Delta exploit generally focuses on a small change or update (delta) in the software code that may have introduced a new vulnerability. The goal of this exploit is to gain unauthorized access, steal data, or damage the target system.
How Delta Exploit Works
Delta exploit works by taking advantage of the differences or changes that occur in software updates. When a software is updated, there is a chance that the update is imperfect and introduces a new security hole. Hackers will analyze these changes and look for ways to exploit them.
The general steps in a delta exploit are as follows:
- Identify Update: Hackers identify the software update that has been made.
- Analyze Change: They analyze the code changes that occurred as a result of the update.
- Find Vulnerabilities: Hackers look for vulnerabilities or security holes in the code changes.
- Developing an Exploit: After discovering a vulnerability, the hacker develops exploit code to exploit the vulnerability.
- Executing the Exploit: The exploit code is executed to gain unauthorized access or damage the target system.
Delta Exploit Case Study
One real-world example of a delta exploit is a case where a software update fixes one bug but unknowingly introduces a new vulnerability. For example, an update to a web application that fixes an XSS (Cross-Site Scripting) bug may inadvertently introduce a new SQL injection vulnerability. An alert hacker can quickly exploit this new vulnerability before the developer notices it and fixes it.
Delta Exploit Prevention
To prevent delta exploits, there are several steps that can be taken:
- Thorough Testing: Before releasing a software update, perform thorough testing to ensure that no new vulnerabilities are introduced.
- Code Change Monitoring: Use a code change monitoring tool to track and analyze every change made to the software.
- Periodic Security Assessments: Conduct regular security assessments to identify and fix security holes before they are exploited by malicious actors.
- Increased Security Awareness: Increase security awareness and training for development teams to understand the importance of security testing and assessments.
Examples of Vulnerable Software
Software that is vulnerable to delta exploits is typically software that receives regular updates and has a complex code base. Some common examples of vulnerable software include:
1. Operating Systems
Large operating systems often receive updates that may fix one vulnerability but inadvertently open another. Vulnerabilities at this level are critical because they can provide full access to the system.
2. Web Applications
- Content Management Systems (CMS) such as WordPress, Joomla, and Drupal: CMSs are frequently updated to add features and fix bugs, but these changes can introduce new vulnerabilities such as SQL injection or XSS.
- Frameworks such as Django and Ruby on Rails: Updates to these web frameworks can fix security holes but can also create new vulnerabilities.
3. Enterprise Software
- ERP Systems (SAP, Oracle): Enterprise Resource Planning systems are often complex and receive many updates, making them vulnerable to delta exploits.
- CRM Systems (Salesforce, Microsoft Dynamics): Frequently updated Customer Relationship Management systems can also be targets for delta exploits.
4. Mobile Apps
- Android and iOS Apps: Apps that are frequently updated on the Google Play Store or Apple App Store may introduce new vulnerabilities with each update.
- Mobile OS (Android and iOS): Mobile operating systems that frequently receive security updates are also vulnerable to delta exploits.
5. Web Browsers
Web browsers are frequently updated to fix bugs and improve security, but each update can also introduce the risk of new vulnerabilities.
6. Network Software
- Router Firmware (Cisco, Netgear): Firmware updates for network devices are often vulnerable to delta exploits due to the complexity and frequency of updates.
- VPN Software (OpenVPN, Cisco AnyConnect): VPN software that is updated to patch security holes may introduce new vulnerabilities.
7. Open Source Software
Updates to widely used open source libraries are often vulnerable due to their large user base and integration complexity.
Real Cases
- Heartbleed Bug
A vulnerability in OpenSSL that emerged after a code update. This exploit allowed an attacker to read memory from an affected server.
- Shellshock
A vulnerability discovered in Bash after several updates, allowed an attacker to run malicious shell commands.
Vulnerability Prevention in Software
Regular Testing and Validation: Perform thorough security testing every time the software is updated.
Continuous Integration/Continuous Deployment (CI/CD): Use CI/CD practices with automated security testing to detect vulnerabilities early.
Monitoring and Rapid Patching: Continuously monitor for suspicious activity and quickly patch when vulnerabilities are discovered.
Regular Code Audits: Conduct regular code audits to find and fix potential vulnerabilities before they are exploited by malicious actors.
With awareness and proactive action, organizations can reduce the risk of delta exploits and keep their software secure.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…