Published on May 24, 2025
What Is DNS Amplification?
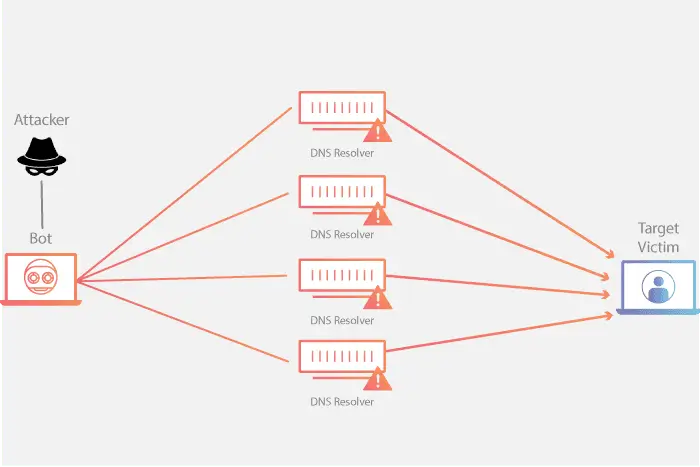
DNS Amplification is a type of Distributed Denial of Service (DDoS) attack that utilizes the Domain Name System (DNS) protocol to increase the amount of traffic directed to the target, causing the target to become overwhelmed and unable to operate properly. This attack works by utilizing open DNS servers that can be accessed by anyone (open resolver) to increase the amount of data sent to the target of the attack.
How DNS Amplification Works
A DNS Amplification attack usually involves the following steps:
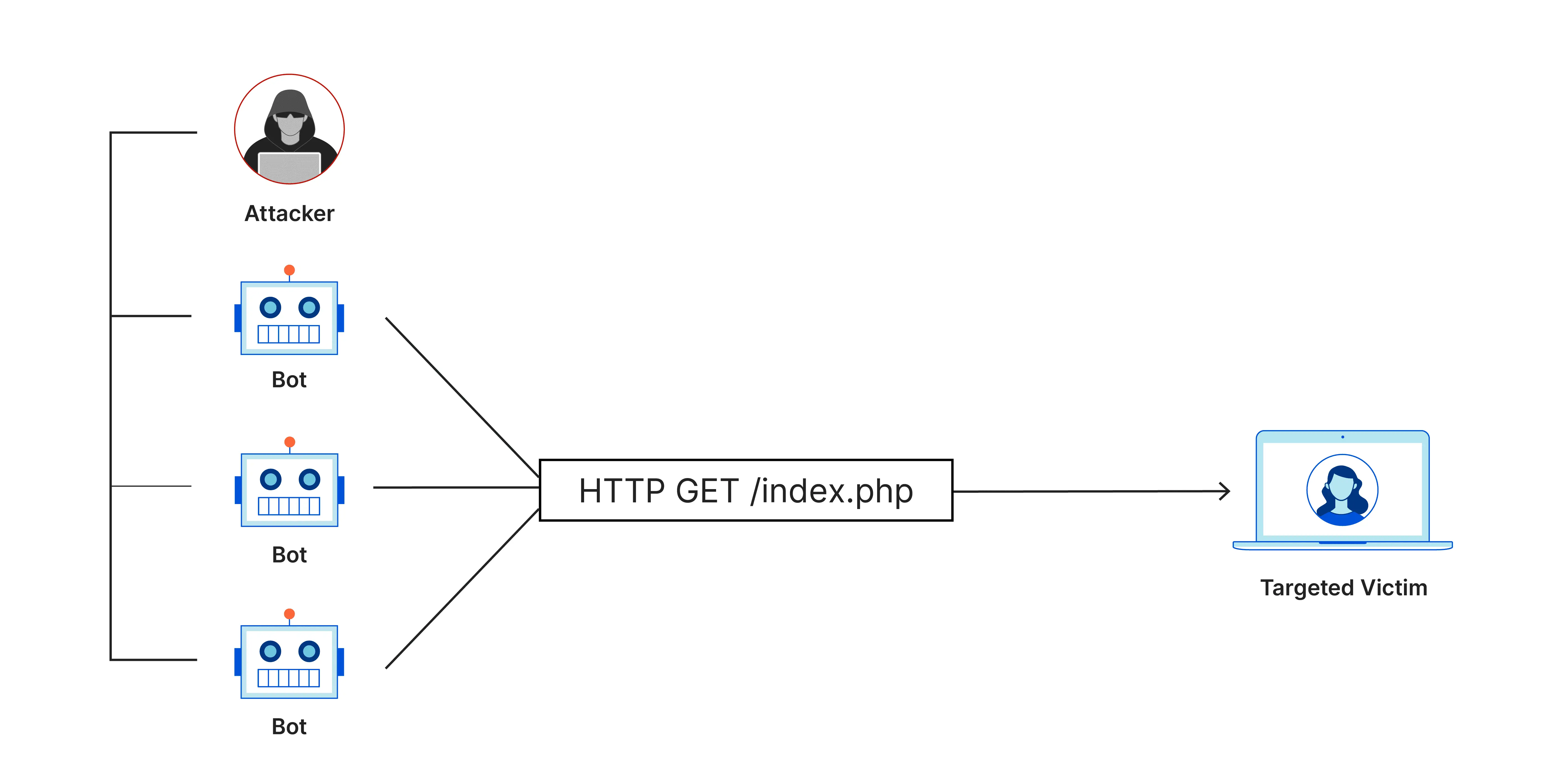
- Attacker Sends a DNS Request: The attacker sends a DNS request to an open DNS server. This request is crafted in such a way that the reply will be much larger than the original request. Typically, attackers use an ANY type DNS request, which requests all information related to a particular domain.
- IP Address Forgery: The DNS request sent by the attacker uses a fake IP address (spoofed IP address) from the target. Thus, when the DNS server sends a reply, the reply is sent to the target, not the attacker.
- DNS Server Sends Amplified Replies: The exposed DNS server sends a much larger reply to the spoofed (target) IP address. Since the reply size is larger than the request, the amount of data the target receives is much larger.
- Target Flooded with Traffic: The target receives a large number of replies from the exposed DNS server, which causes the target’s network and computing resources to become overwhelmed and ultimately unable to serve legitimate requests from other users.
Impact of DNS Amplification
The impact of a DNS Amplification attack can be devastating, especially for organizations that rely on online services. Some of the impacts include:
- Service Disruption: The attacked online service becomes unavailable, resulting in operational disruption and inconvenience to users.
- Financial Loss: Businesses that rely on online services can suffer significant financial losses due to downtime.
- Tainted Reputation: The inability to maintain service availability can damage an organization’s reputation with customers and business partners.
DNS Amplification Mitigation Methods
To prevent and reduce the risk of DNS Amplification attacks, several mitigation steps can be taken:
- DNS Server Configuration: Ensure that the DNS server is not open to the public (non-recursive DNS). Only allow access from authorized IP addresses.
- Rate Limiting: Apply rate limiting to limit the number of requests that can be accepted from a single IP address in a given time period.
- Filter Malicious Requests: Use a firewall and intrusion detection system (IDS) to filter suspicious DNS requests and reject requests from unauthorized IP addresses.
- Monitoring and Logging: Continuously monitor network traffic and DNS server logs to detect suspicious patterns and respond quickly if any abnormal activity is detected.
- Use of Anycast: Using anycast DNS to distribute the traffic load across multiple servers in different geographic locations, reducing the impact of an attack on a single server.
With a good understanding of how DNS Amplification works and the right mitigation steps, organizations can be better prepared to deal with this threat and maintain the availability of their online services.
What are Examples of DNS Amplification Attacks?
One of the most famous examples of a DNS Amplification attack was the attack on Spamhaus in 2013. Here is a detailed explanation of the incident:
Attack on Spamhaus (2013)
Spamhaus is a non-profit organization that aims to combat email spam and provides a blacklist service to block spam sources. In March 2013, Spamhaus was the target of one of the largest DDoS attacks ever recorded to that time. This attack used the DNS Amplification method.
Attack Details
Excessive DNS Requests: The attackers sent a large number of forged DNS requests to various open DNS servers around the world. These requests were designed to generate large DNS responses.
IP Address Forgery: The DNS requests contained fake IP addresses directed to Spamhaus servers. In this way, large responses from open DNS servers were sent to Spamhaus IP addresses.
Scale and Impact: The attack generated a huge amount of data traffic, with peaks reaching around 300 Gbps. Such a large volume of traffic caused serious disruption not only to Spamhaus but also to other parts of the internet infrastructure.
Parties Involved: The attack was allegedly carried out by a group that disagreed with Spamhaus’s anti-spam activities. Cloudflare, a company that provides DDoS mitigation services, helped mitigate the attack.
Impact
- Service Disruption: Spamhaus experienced significant service disruption, affecting its ability to provide a spam blacklist to users worldwide.
- Chain Effect: The attack also impacted the global internet infrastructure, disrupting internet service in many parts of the world due to the large amount of traffic generated.
- Raised Awareness: The incident raised awareness of the serious threat posed by DDoS attacks, particularly the DNS Amplification type of attack.
Lessons Learned from the Spamhaus Attack
- The Importance of DNS Protection: The incident demonstrated the importance of securing DNS servers from being used as amplification tools in DDoS attacks.
- Global Collaboration: Dealing with an attack of this magnitude requires collaboration across internet service providers, DDoS mitigation service providers, and cybersecurity authorities.
- The Need for Robust Infrastructure: The attack highlights the need for stronger and more secure infrastructure to handle sudden and massive spikes in traffic.
The attack on Spamhaus is a clear example of how dangerous DNS Amplification can be if not taken seriously. It also highlights the importance of effective prevention and mitigation measures to protect the global internet infrastructure from such threats.
What is the Difference Between DNS Amplification and DDoS?
DNS Amplification and Distributed Denial of Service (DDoS) are two closely related concepts in the world of cybersecurity, but there are some fundamental differences between the two:
Basic Understanding
DDoS (Distributed Denial of Service):
- Definition: An attack that aims to make a service or system inaccessible to legitimate users by flooding the target with a large amount of unauthorized network traffic.
- How it Works: Attackers use many compromised devices (often called botnets) to send large, continuous traffic to the target. This drains system resources (such as bandwidth, CPU, memory) until the system becomes slow or unresponsive.
DNS Amplification:
- Definition: A type of DDoS attack that exploits weaknesses in the DNS protocol to amplify the amount of traffic directed to the target.
- How it Works: Attackers send forged DNS requests using the target’s IP address to an open DNS server. The DNS server then sends a much larger response than the original request to the target, causing the target to be overwhelmed by the amplified traffic.
Key Differences
Attack Methods:
- DDoS: Uses a variety of methods to flood a target with traffic. These methods include volumetric, protocol, and application attacks. Examples of volumetric attacks include SYN flood, UDP flood, etc.
- DNS Amplification: Specifically uses spoofed DNS requests to amplify traffic to a target.
Amplification:
- DDoS: Does not necessarily involve amplification. Many DDoS attacks simply rely on large amounts of traffic from multiple sources.
- DNS Amplification: Relies on the principle of amplification, where small requests generate much larger replies, magnifying the impact of the attack.
Traffic Sources:
DDoS: Traffic sources can be from multiple compromised devices around the world (botnet).
DNS Amplification: The amplified traffic comes from exposed DNS servers that respond to fake requests sent by the attacker.
Targets:
- DDoS: The target is the system or service that the attacker wants to disrupt. The primary goal is to make the service unavailable to legitimate users.
- DNS Amplification: The target is the system that receives the amplified DNS replies. The primary goal remains the same, which is to make the service unavailable, but the method is through amplification.
Exploited Vulnerabilities:
- DDoS: Can exploit a variety of vulnerabilities in network protocols, applications, or systems.
- DNS Amplification: Specifically exploits vulnerabilities in exposed DNS server configurations that can be used for amplification.
Example Attacks
- Common DDoS: SYN flood, where the attacker sends a large number of SYN (synchronize) requests to the target server with the goal of filling up the connection table and preventing new legitimate connections.
- DNS Amplification: The 2013 Spamhaus attack, in which attackers sent DNS requests with spoofed IP addresses to open DNS servers, resulting in large replies being directed to the target.
Mitigation
- DDoS: Using DDoS mitigation solutions that include firewalls, load balancers, and anti-DDoS cloud services that can detect and absorb attack traffic.
- DNS Amplification: Securing DNS servers with proper configuration, using rate limiting, and implementing filtering for suspicious requests.
By understanding the difference between DNS Amplification and DDoS, organizations can be better prepared to deal with and mitigate these types of cyber threats.
What is Rate Limiting in DNS?
Rate limiting is a technique used to limit the number of requests received or processed by a DNS server in a given time period. Its main purpose is to prevent abuse and protect the server from attacks, such as DDoS attacks or DNS Amplification.
How Does Rate Limiting Work?
Rate limiting in DNS works by setting a limit on the number of requests that can be received or processed from a single source in a given time interval. If the number of requests from that source exceeds the specified limit, the server will either reject the additional requests or respond with an error message.
Rate Limiting Components
- Threshold: The maximum number of requests allowed from a single source in a given time period (e.g., 100 requests per second).
- Window Time: The time period over which the number of requests is counted (e.g., per second, per minute).
- Action on Exceeding Limit: The action taken when the number of requests exceeds a limit, such as rejecting additional requests or returning an error message.
Implementing Rate Limiting in DNS
Rate limiting on a DNS server can be implemented in a variety of ways, including hardware configuration, DNS server software, and network security services. Some common methods include:
- DNS Server Configuration: Many DNS server software, such as BIND, Knot, and PowerDNS, support rate limiting configuration. Administrators can set request limits through configuration settings.
Example of rate limiting configuration in Bash:
rate-limit {
responses-per-second 20;
window 5;
};
- Firewalls and Intrusion Detection Systems (IDS): Firewalls and IDSs can be used to implement rate limiting at the network level. They can monitor DNS traffic and apply limits based on the source IP address.
- Cloud DNS Services: Cloud-based DNS service providers often provide rate limiting as part of their security services. This allows customers to set request limits as needed.
Benefits of Rate Limiting in DNS
- Reduces the Risk of DDoS Attacks: By limiting the number of requests from a single source, rate limiting can reduce the effectiveness of DDoS attacks that attempt to flood a DNS server with excessive traffic.
- Prevent Abuse: Rate limiting helps prevent abuse of DNS server resources by unauthorized users or malware-infected devices.
- Improve Performance and Availability: By controlling the number of requests processed, a DNS server can maintain stable performance and remain available to legitimate users.
Challenges and Considerations
- False Positives: Sometimes, legitimate requests can be rejected if the rate limiting threshold is too low or if there is a surge in legitimate traffic.
- Proper Configuration: Setting the right threshold requires an understanding of normal traffic patterns and potential threats. A threshold that is too high may be ineffective, while a threshold that is too low may be disruptive to legitimate users.
- Scalability: For large networks or services with many users, implementing effective rate limiting can require a scalable and flexible solution.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…