Published on May 24, 2025
What Is a Firewall and Why Is It Important for Network Security?

Firewall is an important component in a network security system that functions as a barrier between internal and external networks, such as the internet. Its function is to prevent unauthorized access and protect data and systems from potential threats.
1. Definition of Firewall
Firewall is a device or software designed to monitor and control network traffic based on predetermined security rules. Firewall acts as a barrier that filters data entering and leaving the network, ensuring that only legitimate data can access the system.
2. Types of Firewalls
There are several types of firewalls that are commonly used, including:
Hardware-Based Firewall: This is a physical device that is connected to the network and monitors and controls data traffic. Usually used by large organizations and internet service providers.
Software-Based Firewall: This firewall is installed on a computer or server and functions to protect individual devices from threats. Usually used on personal computers and servers.
Network Firewall: Used to protect a network from attacks by monitoring traffic between two networks, such as between an internal network and the internet.
Application Firewall: Focuses on protecting specific applications and is often used to secure web applications from attacks such as SQL injection or Cross-Site Scripting (XSS).
3. How a Firewall Works
A firewall works by filtering network traffic based on predetermined rules. These rules typically include criteria such as IP addresses, ports, and protocols. The firewall process can be divided into several steps:
- Packet Inspection: The firewall examines each data packet passing through the network and compares it to the existing rules. Packets that match the rules are allowed in, while packets that do not match are blocked.
- Connection Inspection: In addition to inspecting packets, firewalls can also monitor sessions or connections to ensure that only legitimate sessions are allowed through.
- Application Inspection: Some firewalls, especially application-based ones, can analyze data at the application level to detect and prevent more sophisticated threats.
4. Why is a Firewall Important?
- Protection from External Threats: Firewalls prevent attacks from outside the network, such as hackers or malware, which can damage systems and steal data.
- Access Control: Firewalls help in controlling access to the network, ensuring that only authorized users can access sensitive information.
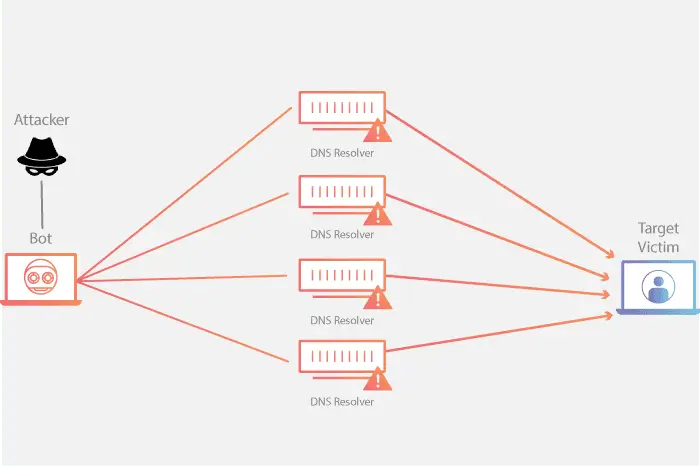
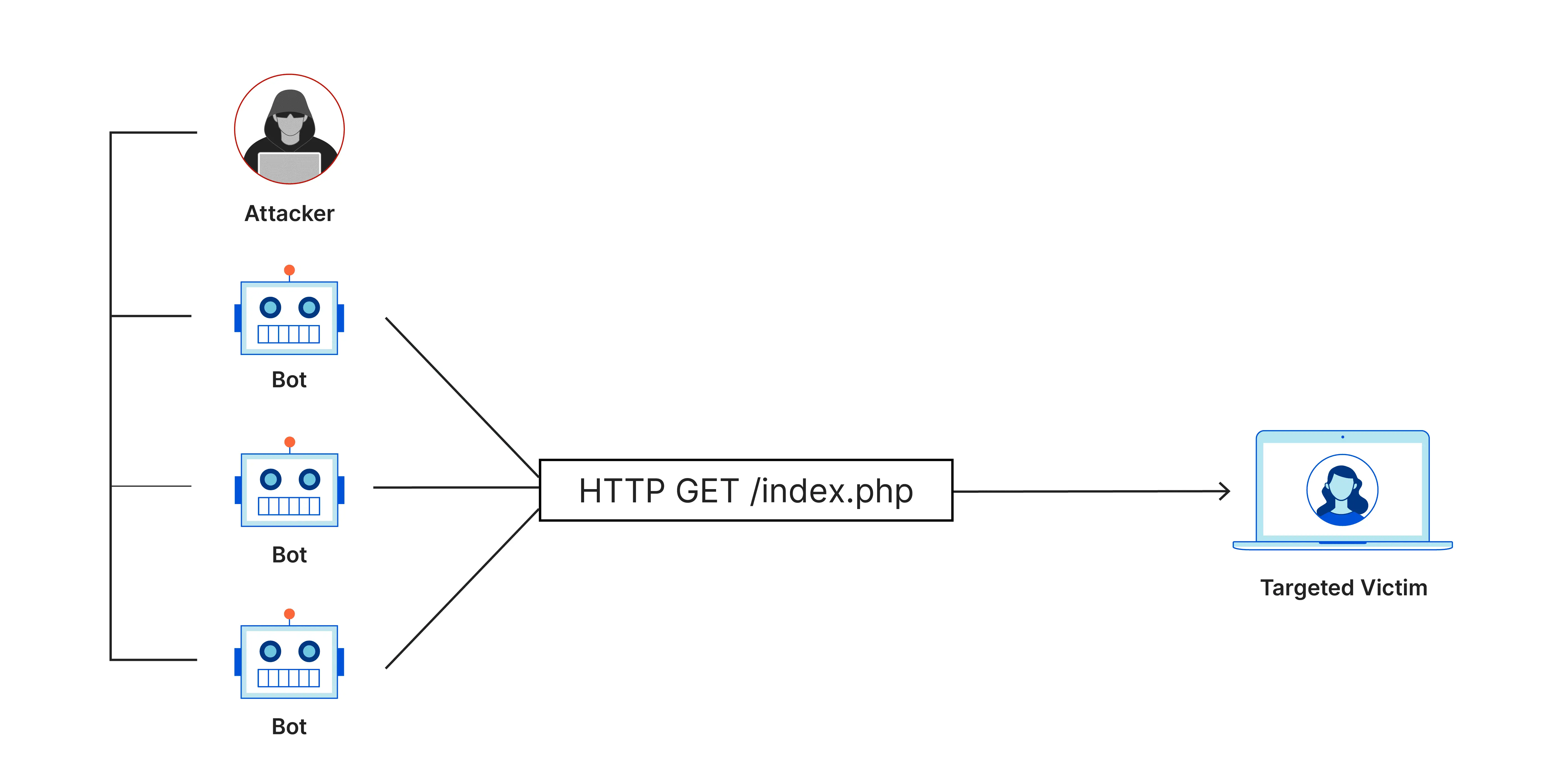
- Network-Based Attack Prevention: Firewalls can identify and prevent various types of network-based attacks, including denial-of-service (DoS) and distributed denial-of-service (DDoS).
- Security Policy Management: With firewalls, organizations can enforce strict security policies, ensuring that data and systems are protected according to corporate standards.
How to Set Up a Firewall?
Properly setting up a firewall is an important step in ensuring the security of your network and systems. Here are some general guidelines for setting up a firewall, which apply to both hardware firewalls, software firewalls, and cloud-based solutions:
1. Preparation and Planning
- Identify Security Needs: Determine what types of data and applications need to be protected, and what potential threats to watch out for.
- Understand Network Topology: Identify the structure of your network, including connected devices, servers, and access points.
- How to Make a Weather Forecast App With Cpp
- How to View WiFi Maps on Websites: Complete Guide
- Understanding DEP (Data Execution Prevention): Definition, Function, and Benefits
- What are the Popular Metasploit Payload Modules that Hackers Often Use?
- Whisper Leak Toolkit Exposes User Prompt Leaks to Popular AI Agents in Encrypted Traffic
2. Firewall Installation
- Hardware Firewall: Install a physical device between the internal and external networks, such as a router or modem.
- Software Firewall: Install the firewall software on your computer or server. Make sure it is updated to the latest version.
- Cloud-Based Firewall: Follow your service provider’s instructions to configure the firewall according to your network’s needs.
3. Configure Firewall Rules
Create Basic Rules
Define basic rules for allowed and blocked traffic. Typically, the basic rules are “block all, allow some”, which means only allowed traffic can enter or leave.
- Allow: Allow traffic from a specific source or destination, such as an email server or a web application.
- Block: Block unnecessary or suspicious traffic.
Port and Protocol Configuration
Specify the port and protocol that your application uses, and set the firewall to allow the required traffic.
- Port: Set the port that your application uses (for example, port 80 for HTTP or port 443 for HTTPS).
- Protocol: Select the required protocol, such as TCP or UDP.
Specify IP Addresses
Set rules based on source and destination IP addresses.
- IP Source: Specify which IPs are allowed or blocked for inbound access.
- IP Destination: Specify the destination IP for outbound traffic.
Set Access Policies
Define access policies based on applications, users, or locations. For example, allow remote access only from specific IP addresses.
4. Deployment and Testing
- Deploy Rules
Deploy the configured rules and make sure the firewall starts filtering traffic according to the defined policies.
- Test Configuration
Perform tests to ensure that the firewall rules are working as expected. Use network testing tools or attack simulations to test the effectiveness of the rules.
5. Monitoring and Maintenance
- Monitor Activity
Use monitoring tools to track traffic and activity on the firewall. This helps in detecting potential threats or abuse.
- Update Rules
Periodically update the firewall rules to reflect changes in network requirements or new threats.
- Apply Security Updates
Make sure the firewall software and hardware firmware are always updated with the latest security patches.
6. Documentation and Training
- Document the Configuration
Record the firewall configuration, the rules applied, and the changes made. This documentation is useful for future maintenance and auditing.
- Train Users
Train IT staff and users on the security policies in place and how to report potential issues.
Additional Tips
- Use Logging
Enable logging on the firewall to record activity and aid in forensic analysis in the event of a security incident.
- Integration with Other Security Systems
Consider integrating the firewall with other security systems, such as an intrusion detection system (IDS) or an intrusion prevention system (IPS), for more comprehensive protection.
By following these steps, you can effectively set up a firewall to protect your network and data from a variety of threats.
How to Test a Firewall?
Testing your firewall is an important step to ensure that your configuration is working as expected and is effective in protecting your network. Here are some methods and tools you can use to test your firewall:
1. Basic Connectivity Test
- Ping: Use the
pingcommand to check that devices on your network are reachable. For example, ping an external IP address to ensure that your firewall isn’t accidentally blocking outgoing connections.
ping 8.8.8.8
- Traceroute: Use the
traceroutecommand (ortracerton Windows) to trace the path that data packets take. This helps ensure that packets aren’t dropped at some point due to firewall rules.
traceroute google.com
2. Test Firewall Rules
- Telnet and Netcat: Use
telnetornetcatto test specific ports and make sure that ports that are supposed to be open or closed are working as per the rules.
telnet [IP address] [port]
nc -zv [IP address] [port]
- Nmap: Use the
nmaptool to perform a port scan and check which ports are open or closed. This can also help identify potential weaknesses in your firewall configuration.
nmap [IP address]
3. Test Application Connections
- Web Browser: Try accessing an application or web service that is connected through the firewall to ensure that HTTP/HTTPS traffic is being forwarded correctly.
- Application Testing Tools: Use application testing tools to ensure that applications that require network access are functioning according to the firewall rules that have been set.
4. Security and Penetration Testing
- Nessus or OpenVAS: Use vulnerability scanning tools such as Nessus or OpenVAS to detect potential vulnerabilities in the firewall and other security configurations.
- Metasploit: Use Metasploit for attack simulations and penetration tests to ensure that the firewall can detect and prevent potential attacks.
5. Simulated Attacks
Perform simulated attacks to test whether the firewall can detect and block attacks such as:
- DDoS Attacks: Try sending a high volume of traffic to test the firewall’s capacity limits.
- SQL Injection or XSS: Test the web application behind the firewall to verify whether the firewall can block application attacks.
6. Monitoring and Logs
- Firewall Logs: Review the firewall logs to ensure that the rules you apply are logging the appropriate activity and that no suspicious activity has been missed.
- Monitoring Tools: Use network monitoring tools to examine traffic passing through the firewall and ensure that traffic that is allowed is in accordance with the rules you set.
7. Live Testing
Ask end users to report if they are having problems accessing a particular application or service. This helps identify issues that may not be detected during automated testing.
8. Periodic Testing
Perform periodic firewall tests to ensure that the configuration remains effective and to detect changes in traffic patterns or potential threats.
Additional Tips
- Document Results: Keep records of test results for further reference and analysis.
- Adjust Configuration: Based on test results, adjust firewall rules to improve security and performance.
- Update and Improve: Always update testing tools and techniques to keep up with the latest developments in security threats.
By performing these tests, you can ensure that your firewall is functioning properly, protecting your network effectively, and handling potential threats as expected.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…