Published on Jun 23, 2025
Understanding SYN Flood: A DDoS Attack That Disrupts Network Performance
SYN Flood is a type of DDoS (Distributed Denial of Service) attack that targets the Transport layer of the OSI (Open System Interconnection) model. This attack aims to disrupt network performance by flooding the target server with a large number of incomplete connection requests, so that system resources become saturated and unable to serve legitimate requests from other users.
How SYN Flood Works
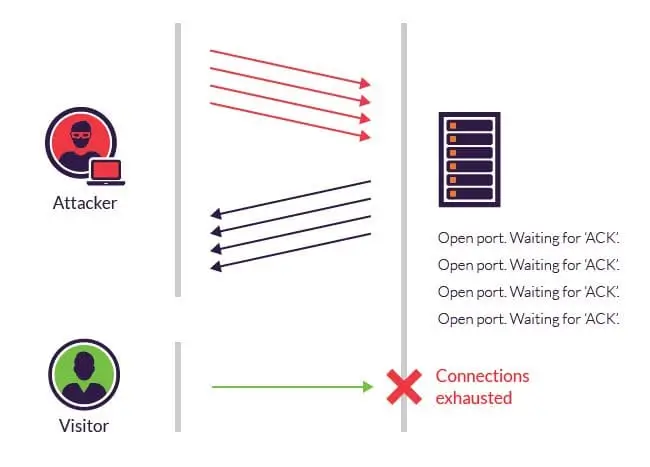
A SYN Flood attack takes advantage of the three-way handshake process used in the TCP (Transmission Control Protocol) protocol to establish a connection. This process involves three basic steps:
SYN (Synchronize): The client sends a SYN packet to the server to initiate a connection.
SYN-ACK (Synchronize-Acknowledge): The server responds with a SYN-ACK packet, indicating that the server is ready to establish a connection.
ACK (Acknowledge): The client sends a final ACK packet to complete the three-way handshake, and the connection is established.
In a SYN Flood attack, the attacker sends a large number of SYN packets to the target server, but never responds to the SYN-ACK packets sent by the server. As a result, the server is left waiting for a response from the client that never comes, leaving many half-open connections in the system. If the number of these half-open connections exceeds the server’s capacity, legitimate connections from other users cannot be processed, causing performance degradation or even service failure.
Impact of SYN Flood Attacks
The primary impact of a SYN Flood attack is performance degradation or complete failure of the attacked server. This can result in:
- Service Unavailability: Legitimate users are unable to access services provided by the server because system resources are used up to handle fraudulent requests.
- Loss of Revenue: For online businesses, downtime caused by a SYN Flood attack can result in lost revenue and damage the company’s reputation.
- Mitigation Cost: Addressing and preventing SYN Flood attacks requires investment in security hardware and software, which can add to a company’s operational costs.
Mitigation Methods
To protect a network from a SYN Flood attack, several mitigation methods can be implemented, including:
- Syn Cookies: This technique allows the server to manage connections without storing state information in memory until the three-way handshake is complete. In this way, the server can avoid running out of resources due to a large number of half-open connections.
- Rate Limiting: Limiting the number of SYN connections received by a server in a given time period can help prevent resource saturation.
- Firewall and Intrusion Detection System (IDS): Firewall and IDS can be configured to detect and block suspicious traffic that resembles a SYN Flood attack.
- Load Balancer: Using a load balancer to distribute network traffic across multiple servers can reduce the load on a single server and increase resilience to attacks.
How Does TCP Work?
Transmission Control Protocol (TCP) is one of the main protocols in the Internet protocol suite used to send data across computer networks. TCP provides reliable and ordered data delivery services, which are essential for applications such as web browsing, email, and file transfer. Here is an explanation of how the TCP protocol works:
1. Three-Way Handshake
This process is used to establish a connection between the client and the server before data is sent. The three-way handshake consists of three steps:
SYN (Synchronize):
- The client sends a SYN packet to the server to initiate the connection.
- This packet contains the initial sequence number chosen by the client.
SYN-ACK (Synchronize-Acknowledge):
- The server responds with a SYN-ACK packet.
- This packet contains the sequence number chosen by the server and the client’s sequence number increased by one, indicating that the server received the client’s SYN packet.
ACK (Acknowledge):
- The client sends a final ACK packet to the server.
- This packet contains the server’s sequence number incremented by one, completing the three-way handshake process.
- The TCP connection is now established and ready to transfer data.
2. Data Delivery
Once the connection is established, data can be transferred between the client and server. TCP ensures that data is delivered reliably and in the correct order through several mechanisms:
Segmentation and Reassembly:
- Data is divided into smaller segments.
- Each segment is assigned a sequence number to ensure that the data can be reassembled correctly at the receiving end.
Acknowledgment:
- Each time a data segment is received, the receiver sends an acknowledgment (ACK) back to the sender.
- If the sender does not receive an ACK within a certain amount of time, the segment is considered lost and will be resent.
Sliding Window:
- TCP uses a sliding window mechanism to regulate how much data can be sent before having to wait for an ACK.
- The window size can be varied to optimize delivery speed and avoid network congestion.
3. Connection Closing
This process is used to close a TCP connection after the data transfer is complete. Closing a connection also involves a series of messages:
FIN (Finish):
- One party (usually the client) sends a FIN packet to initiate the connection closing.
- This packet indicates that no more data will be sent from the FIN sender.
ACK (Acknowledge):
- The receiving party responds with an ACK packet to acknowledge receipt of the FIN packet.
FIN from receiver:
- The receiver then sends a FIN packet to indicate that they also have no more data to send.
ACK from sender:
- The sender responds with a final ACK packet to acknowledge receipt of the FIN packet from the receiver.
- The TCP connection is now closed.
4. Other TCP Features
Flow Control:
- TCP uses a flow control mechanism to prevent the sender from flooding the receiver with data faster than it can process it.
Error Detection:
- TCP uses a checksum on each segment to detect data errors during transmission.
- Corrupted segments are rejected, and the sender must resend them.
Congestion Control:
- TCP implements an algorithm to control network congestion by adjusting the speed of data transmission based on network conditions.
What is the Difference Between TCP and UDP?
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two major communication protocols in computer networks that are used to send data between devices. Although both function to send data, there are some fundamental differences in how they work and their characteristics. Here are the main differences between TCP and UDP:
1. Reliability
TCP:
- High Reliability: TCP ensures reliable data delivery. Data sent using TCP is guaranteed to arrive at its destination in the correct order. If a data segment is lost or corrupted, TCP will retransmit the segment.
- Acknowledgment: Each data segment received by the receiver is acknowledged by sending an acknowledgment (ACK) message back to the sender.
- Error Detection and Correction: TCP uses a checksum to detect errors and resend corrupted or lost data.
UDP:
- Low Reliability: UDP does not guarantee reliable data delivery. Data sent using UDP may be lost, corrupted, or arrive at its destination in the wrong order.
- No Acknowledgment: UDP does not send an acknowledgment message. There is no mechanism for retransmitting lost or corrupted data.
- Error Detection Only: UDP also uses a checksum, but only to detect errors, with no automatic repair mechanism.
2. Connection Method
TCP:
- Connection-Oriented: TCP is a connection-oriented protocol. Before data is sent, TCP establishes a connection through a three-way handshake process. After data is sent, the connection is closed with a connection-closing procedure.
- Stateful: TCP maintains connection state during communication, keeping track of segments that have been sent and received.
UDP:
- Connectionless: UDP is a non-connection-oriented protocol. There is no handshake or connection-closing process. Data is sent in the form of datagrams without requiring a previous connection.
- Stateless: UDP does not maintain connection state, making it lighter and faster.
3. Speed and Overhead
TCP:
- High Overhead: TCP has higher overhead due to handshake, acknowledgment, and error control mechanisms.
- Slower: TCP tends to be slower than UDP due to retransmission of lost data and connection setup.
UDP:
- Low Overhead: UDP has lower overhead because there is no handshake or acknowledgment mechanism.
- Faster: Because there is no retransmission or connection setup, UDP is faster and more efficient in sending data.
4. Usage
TCP:
- Applications That Require Reliability: TCP is used in applications that require reliable and sequential data delivery, such as web browsing (HTTP/HTTPS), email (SMTP), file transfer (FTP), and terminal sessions (SSH).
UDP:
- Applications That Require Speed: UDP is used in applications that require fast data delivery and are tolerant of data loss, such as video/audio streaming (VoIP, media streaming), online gaming, and other real-time applications.
5. Contoh Penggunaan
TCP:
- Web Browsing: HTTP/HTTPS
- Email: SMTP, IMAP, POP3
- File Transfer: FTP
- Remote Access: SSH, Telnet
UDP:
- Video Streaming: RTP (Real-time Transport Protocol)
- Audio Streaming: VoIP (Voice over IP)
- Game Online: Pengiriman data game
- DNS: Permintaan dan respon DNS
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…