Published on May 24, 2025
Getting to Know xmlrpc.php and Its Security Exploits
In the world of cybersecurity, the xmlrpc.php file in WordPress is often targeted by attackers. xmlrpc.php is a default WordPress file that allows external communication with the WordPress site via the XML-RPC (Remote Procedure Call) protocol. Basically, this file allows users or third-party applications to interact with the WordPress site without having to log in through the WordPress admin panel. For example, the WordPress mobile application or services that perform automatic synchronization.
However, this convenience opens up a gap for cybercriminals who want to exploit the WordPress system. Attacks on xmlrpc.php can involve several methods, including brute force, DDoS (Distributed Denial of Service) attacks, to remote code execution exploit attacks. This article will discuss the ins and outs of the xmlrpc.php file, how attacks can be carried out, and methods to protect WordPress sites from this security risk.
What is xmlrpc.php?
In essence, xmlrpc.php is a protocol that allows external applications to communicate with WordPress using XML as the data format and HTTP as the transport medium. With this protocol, external applications can perform various actions, such as publishing articles, editing content, or getting information from the WordPress site.
This feature is very useful for applications that require dynamic interaction without having to be tied to the site interface. However, if not set up properly, this file actually opens up security holes that can be exploited for cyber attacks.
Types of Attacks Involving xmlrpc.php
Here are some types of attacks that exploit the xmlrpc.php vulnerability in WordPress sites:
- Brute Force Attack
A brute force attack is a technique often used to repeatedly guess usernames and passwords until they find the right combination. xmlrpc.php provides the system.multicall function that allows HTTP requests to send multiple login requests in one send. This makes brute force attacks more effective, because the perpetrator can make thousands of attempts in a short time without requiring many requests.
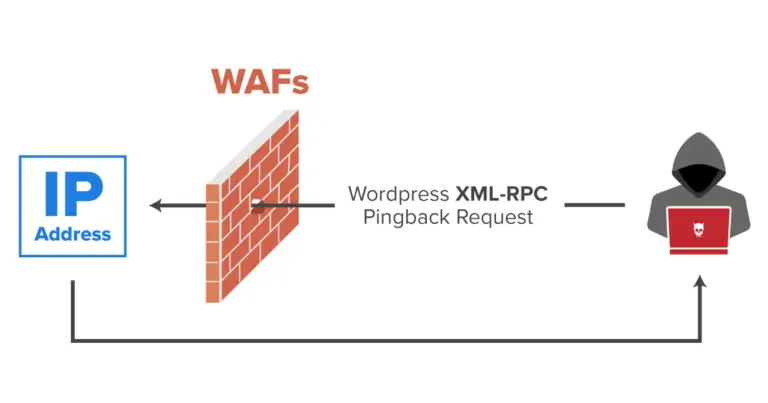
- DDoS Attacks via Pingback
One of the features in XML-RPC is pingback, which is used to notify other sites if there are articles that refer to their content. However, this feature can be manipulated to carry out DDoS attacks. By sending many pingback requests to different sites, attackers can cause the server to be overwhelmed and even make the target site inaccessible.
- Remote Code Execution Exploitation
In more severe cases, some vulnerabilities in xmlrpc.php can be used to execute code on the server. This can happen when the xmlrpc.php file is not updated or has an unpatched security hole. This attack allows attackers to run specific commands on the server and has the potential for major impact.
xmlrpc.php Attack Case Studies
In previous years, there have been several cases where the xmlrpc.php file was exploited for large-scale attacks. One such case occurred in 2015, when a botnet directed attacks on millions of WordPress sites through this file. The botnet exploited the pingback feature to launch DDoS attacks on the target sites, resulting in downtime and high load on the servers.
In addition, in several cases, attackers have also exploited the xmlrpc.php file to hijack sites, plant malware, and steal sensitive data. This vulnerability is a warning for many WordPress site owners to be more vigilant about the XML-RPC feature.
How to Secure xmlrpc.php
Given the importance of securing this file, there are several methods that can be done to protect WordPress sites from xmlrpc.php exploits.
- Disable xmlrpc.php When Not Used
If you do not need access via external applications or XML-RPC features, disabling the xmlrpc.php file can be the first step. You can do this by deleting or blocking access to this file via .htaccess.
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
By adding the above command to the .htaccess file, you can block access to the xmlrpc.php file completely.
- Using a WordPress Security Plugin
There are several WordPress security plugins that automatically detect and block suspicious access attempts to xmlrpc.php. Plugins like Wordfence or Sucuri offer protection that includes restricting access to this file. They can also monitor for suspicious activity, including excessive login attempts via xmlrpc.php.
- IP Restriction for xmlrpc.php
If you still need the XML-RPC feature but want to restrict access, you can restrict only certain IPs from having permission to access this file. This can be done by adding a rule in .htaccess.
<Files xmlrpc.php>
order deny,allow
deny from all
allow from xxx.xxx.xxx.xxx
</Files>
Replace xxx.xxx.xxx.xxx with the IP addresses you want to grant access to. This method ensures that only certain IPs can use the XML-RPC feature, thus preventing attacks from other sources.
- Utilize a Web Application Firewall (WAF)
A Web Application Firewall (WAF) such as Cloudflare or Sucuri can help protect your WordPress site by filtering incoming traffic. A WAF can detect and block suspicious requests that try to exploit the xmlrpc.php file, including brute force and DDoS attacks. With WAF, you have additional protection that focuses not only on xmlrpc.php, but also on your entire WordPress site.
- Update WordPress Regularly
Regular updates to WordPress and plugins are essential. WordPress regularly updates core files and patches any security holes it finds, including xmlrpc.php. By keeping WordPress and plugins up to date, you can reduce the risk of being exploited through known vulnerabilities.
Why is xmlrpc.php Still Needed?
Despite its security risks, xmlrpc.php is not being removed from WordPress. This file is still important for some users who need API access to their WordPress site, for example for WordPress mobile applications or for integration with third-party services. Therefore, security measures such as restricting access or using WAF are very helpful in maintaining the balance between functionality and security.
Conclusion
The xmlrpc.php file can indeed improve the functionality and external interaction of a WordPress site, but it also has risks if not managed carefully. With features like multicall and pingback, this file is an attractive target for attackers looking to launch brute force, DDoS, or even remote code execution attacks.
Steps like disabling xmlrpc.php when not needed, using a security plugin, or restricting IP access can help improve the security of your WordPress site. By understanding the risks and how to mitigate them, WordPress site owners can optimize XML-RPC functionality without compromising security.
Keep an eye on WordPress security developments and keep your site updated to keep it safe from attacks that exploit the xmlrpc.php file.
That’s all the articles from Admin, hopefully useful… Thank you for stopping by…



